As people come online, will they be secure? Cybersecurity is a fundamental element of universal access to meaningful connectivity, allowing people to safely come online to carry out critical day-to-day functions. Because cybersecurity has a broad field of application, cutting across many industries and various sectors, ITU's global cybersecurity index displays each country’s level of development or engagement in this issue, assessed along five pillars – (i) legal measures, (ii) technical measures, (iii) organizational measures, (iv) capacity development, and (v) cooperation – and then aggregated into an overall score. As Figure 12 illustrates, although some LDCs are making progress in responding to cybersecurity challenges, the majority rank poorly in this area.

Many challenges today erode online trust and prevent the digital society from operating at its full potential. Global losses due to cybercrime are estimated to range from USD 1 trillion[43] to as high as 6 trillion[44].
Activating legal and regulatory frameworks to address this problem includes establishing legislation that identifies what constitutes illicit activities in cyberspace; defining the necessary procedural tools to enforce such legislation through investigations and prosecutions; determining cybersecurity baselines and compliance mechanisms for a set of national stakeholders; and devising procedures to ensure consistency with international obligations.
Why Cybersecurity in Focus Area 1:
The requirement to look at the implications of cyberthreats remains valid for all four of the focus areas. However, the reason for keeping cybersecurity as a pillar in Focus Area 1, ‘ACCESS: Connecting people everywhere’, is to highlight some of the key areas from a deployment perspective and look at the safety and resiliency of the critical infrastructure from a national perspective. To cover further aspects of cyberthreats and associated cybersecurity elements, each of the other focus areas includes applicable key points and prospective approaches for handling the requirements.
Key issue: CIRT/CERT deployments
Effective mechanisms and institutional structures at the national level are necessary to deal with cyber risks and incidents reliably. Computer incident response teams (CIRTs) or computer emergency response teams (CERTs) enable countries to respond to incidents using a centralized contact point and promote quick and systematic action, empowering governments to learn from experience and build their cybersecurity resilience.
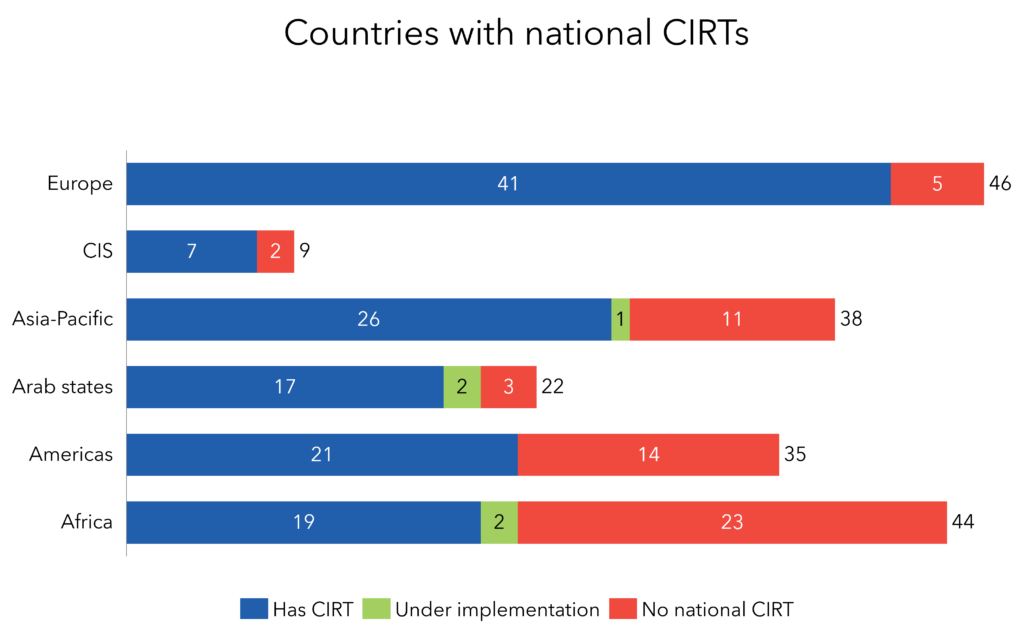
Potential interventions: CIRT/CERTs
CIRTs or CERTs enable responses to incidents at the national level. These teams should be developed and implemented by the government, although private parties can be engaged in the process of setting them up. In addition, sector-specific CIRTs should be established, e.g. for health service providers or law enforcement.
Key issue: Cybersecurity capacity – tools and metrics, training and skills gap
It is increasingly important to provide training programmes in cybersecurity to address the needs of various sectors. Cybersecurity analysts predicted that there were between 3.5 million and 4 million[46] cybersecurity jobs left unfilled globally in 2021. Despite this projected gap, a significant number of countries are yet to develop sector-specific training, and over 50 per cent of countries lack programmes tailored towards specific sectors or professions such as legal actors, MSMEs, private companies, and government officials. The lack of affordable software licences for security and productivity software, tools, and technologies must also be addressed.
Potential interventions:
A) Cybersecurity capacity and expertise
Securing the cyber domain by building cybersecurity capacity and expertise is another key activity. Cybersecurity professionals can advance this knowledge through sector-specific educational programmes and training. Primary and secondary school curricula should include cybersecurity courses to equip children and youth with the fundamentals to navigate digital technologies safely. Improving public awareness of cybersecurity essentials in different industries and across all groups of society is vital. Countries can promote cybersecurity in the private sector by including standards for it in contracts or through incentive mechanisms such as tax holidays or discounts based on cybersecurity parameters. These will encourage private sector actors to prioritize cybersecurity within their operational structures and processes, which in turn will improve a country’s cybersecurity posture in the short, medium, and long term.
B) Cooperative approach
Cybersecurity remains a transnational issue due to the increasing interconnection and correlated infrastructures. The security of the global cyber-ecosystem cannot be guaranteed or managed by any single stakeholder. National, regional, and international cooperation are required to extend the reach and impact of cybersecurity. There is a need to have bilateral or multilateral cooperation and PPPs, and most of the LDCs lack these fundamentals. According to ITU’s global cybersecurity index (GCI), in Africa, only 20 countries have either signed or are in the process of entering into multilateral cybersecurity agreements.[47]
C) Multisector and multilateral harmonization
Cybersecurity risks are borderless and independent of sector or industry due to ever-increasing interconnections and correlated infrastructure. Collaboration helps the harmonization of security measures across the board. Both bilateral and multilateral agreements are crucial in codifying norms and behaviours as well as enhancing international cooperation on cybersecurity. PPPs can facilitate the exchange and implementation of actionable intelligence and good practice. To continue building on the global standards and keep up to date with new developments, stakeholders should host and engage in international activities like cybersecurity conferences, workshops, partnerships and conventions.
Key issue: Protection and resilience of critical infrastructure
Critical infrastructure such as ICT networks, electrical grids, water purification plants, and transportation systems continue to face cybersecurity risks, and ensuring the continuity of operations at the national level is an ongoing challenge for countries. The consequences of an incident impacting critical infrastructure are potentially devastating, and national cybersecurity postures should result in greater attention to risk management efforts intended to reduce the likelihood and escalation of a high-consequence event. As an example, in Africa, only 10 countries have a strategy that addresses both critical infrastructure and resiliency.[48] More governments are in the process of defining such strategies, but many others do not address these elements.
Potential interventions:
A) Cybersecurity strategy
The national cybersecurity position and current practices need to be studied to capture the status of the measures and policies that are in place. This will include an analysis and assessment of the existing cybersecurity risk landscape and the strengths and weakness in the critical national infrastructure. Thereafter, an incident protocol should be set up to monitor and coordinate the responses to any national cyberattacks or threats. In addition, response models aligned to sector-specific requirements (e.g. cyberterrorism against airports or threats to the ICT sector from penetration or denial of service) should be developed and continuously improved.
B) ICT network resilience and recovery following disasters
Disaster-resilient ICT infrastructure can save lives and reduce loss and damage. Extreme weather events, earthquakes, tsunamis, and pandemics, as well as oil spills and other human-made hazards, pose continued challenges to countries and communities. ICTs are crucial for monitoring the environment, analysing information, delivering early warnings, and facilitating the timely flow of vital information in the aftermath of disasters.
Spotlight
The availability of data on network presence and operational status has helped first responders to quickly coordinate actions on the ground. The ITU Disaster Connectivity Map delivers near-real-time information on connectivity gaps and supports decision-making by first responders about where telecommunication network services need to be restored. [49]
Commit to a pledge on our Pledging Platform here. See guidelines on how to make your pledge in Pledging for Universal Meaningful Connectivity and example pledges here
Footnotes
[42] ITU. (2021). Global Cybersecurity Index 2020/2021 Report Release.
[43] Smith, Z. M., Lostri, E., & Lewis, J. A. (2020). The Hidden Costs of Cybercrime.
[44] Cybercrime Magazine. (2020). Cybercrime To Cost The World $10.5 Trillion Annually By 2025
[45] ITU. (2021). Global Cybersecurity Index 2020
[46] New York Times. (2018). The mad dash to find a cybersecurity force.
[47] ITU. (2021). Global Cybersecurity Index 2020.
[48] ITU. (2021). Global Cybersecurity Index 2020.
[49] ITU. (2020). Disaster Connectivity Maps.