Page 273 - ITU-T Focus Group IMT-2020 Deliverables
P. 273
ITU-T Focus Group IMT-2020 Deliverables 4
Figure 14 – In-network Caching
3) Gap E.13 ICN Security (authentication and encryption)
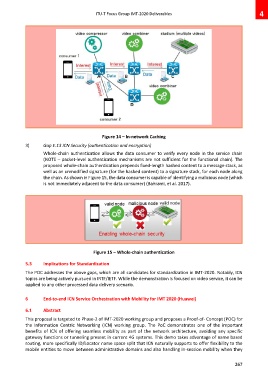
Whole-chain authentication allows the data consumer to verify every node in the service chain
(NOTE – packet-level authentication mechanisms are not sufficient for the functional chain). The
proposed whole-chain authentication prepends fixed-length hashed content to a message stack, as
well as an unmodified signature (for the hashed content) to a signature stack, for each node along
the chain. As shown in Figure 15, the data consumer is capable of identifying a malicious node (which
is not immediately adjacent to the data consumer) (Bahrami, et al. 2017).
Figure 15 – Whole-chain authentication
5.3 Implications for Standardization
The POC addresses the above gaps, which are all candidates for standardization in IMT-2020. Notably, ICN
topics are being actively pursued in IRTF/IETF. While the demonstration is focused on video service, it can be
applied to any other processed data delivery scenario.
6 End-to-end ICN Service Orchestration with Mobility for IMT 2020 (Huawei)
6.1 Abstract
This proposal is targeted to Phase-2 of IMT-2020 working group and proposes a Proof-of- Concept (POC) for
the Information Centric Networking (ICN) working group. The PoC demonstrates one of the important
benefits of ICN of offering seamless mobility as part of the network architecture, avoiding any specific
gateway functions or tunneling present in current 4G systems. This demo takes advantage of name based
routing, more specifically ID/Locator name space split that ICN naturally supports to offer flexibility to the
mobile entities to move between administrative domains and also handling in-session mobility when they
267