Page 219 - Kaleidoscope Academic Conference Proceedings 2020
P. 219
Industry-driven digital transformation
be something like Zigbee or Bluethooth low energy, and split
the uhealth system into tiers based on the task they are in
charge of completing with the final tier reporting its data to
the cloud.
3. SYSTEM DESIGN
The count-min sketch wouldn’t scale well for IoT because it
would only count an aggregate of incoming events while
increasing the likelihood of collisions with the increase of
data even with the added number of hash functions to reduce
the number of collisions. As for the hyper log log sketch it
wouldn’t be much help in this particular scenario because it
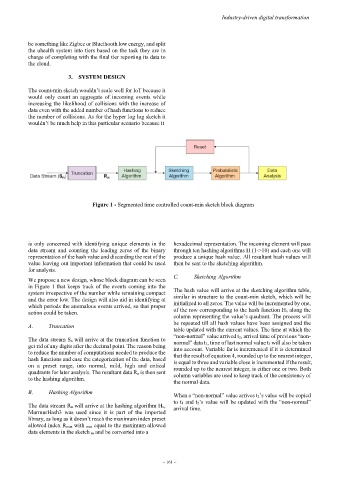
Figure 1 - Segmented time controlled count-min sketch block diagram
is only concerned with identifying unique elements in the hexadecimal representation. The incoming element will pass
data stream and counting the leading zeros of the binary through ten hashing algorithms H (1->10) and each one will
representation of the hash value and discarding the rest of the produce a unique hash value. All resultant hash values will
value leaving out important information that could be used then be sent to the sketching algorithm.
for analysis.
C. Sketching Algorithm
We propose a new design, whose block diagram can be seen
in Figure 1 that keeps track of the events coming into the
system irrespective of the number while remaining compact The hash value will arrive at the sketching algorithm table,
and the error low. The design will also aid in identifying at similar in structure to the count-min sketch, which will be
which periods the anomalous events arrived, so that proper initialized to all zeros. The value will be incremented by one,
action could be taken. of the row corresponding to the hash function H n along the
column representing the value’s quadrant. The process will
be repeated till all hash values have been assigned and the
A. Truncation
table updated with the current values. The time at which the
“non-normal” value arrived t2, arrival time of previous “non-
The data stream S n will arrive at the truncation function to normal” data t1, time of last normal value t3 will also be taken
get rid of any digits after the decimal point. The reason being into account. Variable far is incremented if it is determined
to reduce the number of computations needed to produce the that the result of equation 4, rounded up to the nearest integer,
hash functions and ease the categorization of the data, based is equal to three and variable close is incremented if the result,
on a preset range, into normal, mild, high and critical rounded up to the nearest integer, is either one or two. Both
quadrants for later analysis. The resultant data R n is then sent column variables are used to keep track of the consistency of
to the hashing algorithm. the normal data.
B. Hashing Algorithm
When a “non-normal” value arrives t2’s value will be copied
to t 1 and t 2’s value will be updated with the “non-normal”
The data stream R n will arrive at the hashing algorithm H n, arrival time.
MurmurHash3 was used since it is part of the imported
library, as long as it doesn’t reach the maximum index preset
allowed index Rmax with max equal to the maximum allowed
data elements in the sketch m and be converted into a
– 161 –