Page 52 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 52
11 OVERALL OBSERVATIONS AND RECOMMENDATIONS
11�1 For Entities Building and Operating Distributed Ledger Platforms Internally
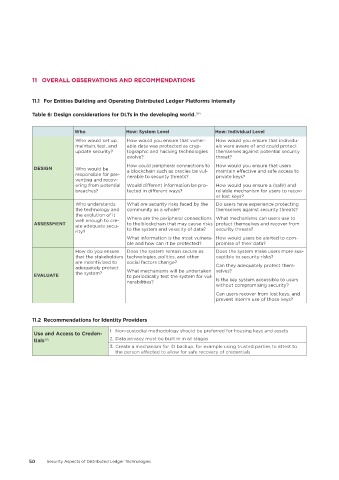
Table 6: Design considerations for DLTs in the developing world� 384
Who How: System Level How: Individual Level
Who would set up, How would you ensure that vulner- How would you ensure that individu-
maintain, test, and able data was protected as cryp- als were aware of and could protect
update security? tographic and hacking technologies themselves against potential security
evolve? threat?
How could peripheral connections to How would you ensure that users
DESIGN Who would be a blockchain such as oracles be vul- maintain effective and safe access to
responsible for pre- nerable to security threats? private keys?
venting and recov-
ering from potential Would different information be pro- How would you ensure a (safe) and
breaches? tected in different ways? reliable mechanism for users to recov-
er lost keys?
Who understands What are security risks faced by the Do users have experience protecting
the technology and community as a whole? themselves against security threats?
the evolution of it
well enough to cre- Where are the peripheral connections What mechanisms can users use to
ASSESSMENT ate adequate secu- to the blockchain that may cause risks protect themselves and recover from
rity? to the system and veracity of data? security threats?
What information is the most vulnera- How would users be alerted to com-
ble and how can it be protected? promise of their data?
How do you ensure Does the system remain secure as Does the system make users more sus-
that the stakeholders technologies, politics, and other ceptible to security risks?
are incentivized to social factors change?
Can they adequately protect them-
adequately protect What mechanisms will be undertaken selves?
EVALUATE the system? to periodically test the system for vul-
nerabilities? Is the key system accessible to users
without compromising security?
Can users recover from lost keys, and
prevent interim use of those keys?
11�2 Recommendations for Identity Providers
Use and Access to Creden- 1. Non-custodial methodology should be preferred for housing keys and assets
tials 385 2. Data privacy must be built in in all stages
3. Create a mechanism for ID backup, for example using trusted parties to attest to
the person affected to allow for safe recovery of credentials
50 Security Aspects of Distributed Ledger Technologies