Page 53 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 53
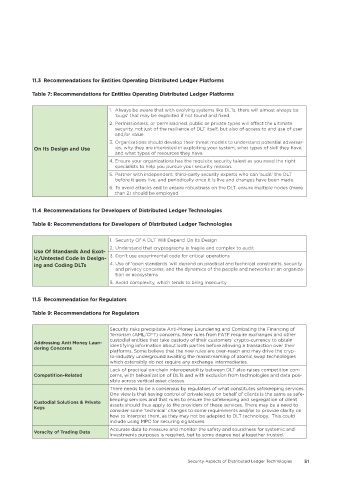
11�3 Recommendations for Entities Operating Distributed Ledger Platforms
Table 7: Recommendations for Entities Operating Distributed Ledger Platforms
1. Always be aware that with evolving systems like DLTs, there will almost always be
‘bugs’ that may be exploited if not found and fixed.
2. Permissionless, or permissioned, public or private types will affect the ultimate
security, not just of the resilience of DLT itself, but also of access to and use of user
and/or value
3. Organizations should develop their threat models to understand potential adversar-
On Its Design and Use ies, why they are interested in exploiting your system; what types of skill they have;
and what types of resources they have.
4. Ensure your organizations has the requisite security talent as you need the right
specialists to help you pursue your security mission.
5. Partner with independent, third-party security experts who can ‘audit’ the DLT
before it goes live, and periodically once it is live and changes have been made.
6. To avoid attacks and to ensure robustness on the DLT, ensure multiple nodes (more
than 2) should be employed
11�4 Recommendations for Developers of Distributed Ledger Technologies
Table 8: Recommendations for Developers of Distributed Ledger Technologies
1. Security Of A DLT Will Depend On Its Design
2. Understand that cryptography is fragile and complex to audit
Use Of Standards And Exot-
ic/Untested Code In Design- 3. Don’t use experimental code for critical operations
ing and Coding DLTs 4. Use of ‘open standards ‘will depend on practical and technical constraints, security
and privacy concerns, and the dynamics of the people and networks in an organiza-
tion or ecosystems
5. Avoid complexity, which tends to bring insecurity
11�5 Recommendation for Regulators
Table 9: Recommendations for Regulators
Security risks precipitate Anti-Money Laundering and Combating the Financing of
Terrorism (AML/CFT) concerns. New rules from FATF require exchanges and other
custodial entities that take custody of their customers’ crypto-currency to obtain
Addressing Anti Money Laun-
dering Concerns identifying information about both parties before allowing a transaction over their
platforms. Some believe that the new rules are over-reach and may drive the cryp-
to-industry underground awaiting the mainstreaming of atomic swap technologies
which ostensibly do not require any exchange intermediaries.
Lack of practical on-chain interoperability between DLT also raises competition con-
Competition-Related cerns, with balkanization of DLTs and with exclusion from technologies and data pos-
sible across vertical asset classes.
There needs to be a consensus by regulators of what constitutes safekeeping services.
One view is that having control of private keys on behalf of clients is the same as safe-
keeping services and that rules to ensure the safekeeping and segregation of client
Custodial Solutions & Private assets should thus apply to the providers of those services. There may be a need to
Keys
consider some ‘technical’ changes to some requirements and/or to provide clarity on
how to interpret them, as they may not be adapted to DLT technology. This could
include using MPC for securing signatures.
Accurate data to measure and monitor the safety and soundness for systemic and
Veracity of Trading Data
investments purposes is required, but to some degree not altogether trusted.
Security Aspects of Distributed Ledger Technologies 51