Page 47 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 47
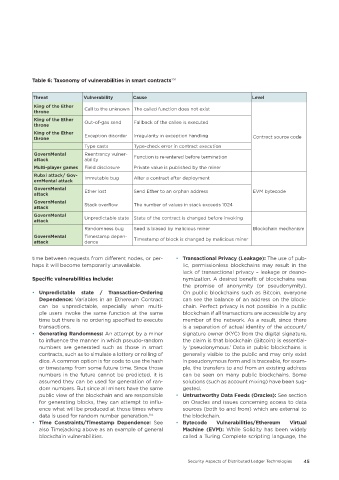
Table 6: Taxonomy of vulnerabilities in smart contracts 350
Threat Vulnerability Cause Level
King of the Ether Call to the unknown The called function does not exist
throne
King of the Ether Out-of-gas send Fallback of the callee is executed
throne
King of the Ether
throne Exception disorder Irregularity in exception handling Contract source code
Type casts Type-check error in contract execution
GovernMental Reentrancy vulner-
attack ability Function is re-entered before termination
Multi-player games Field disclosure Private value is published by the miner
Rubxi attack/ Gov- Immutable bug Alter a contract after deployment
ernMental attack
GovernMental Ether lost Send Ether to an orphan address EVM bytecode
attack
GovernMental
attack Stack overflow The number of values in stack exceeds 1024
GovernMental Unpredictable state State of the contract is changed before invoking
attack
Randomness bug Seed is biased by malicious miner Blockchain mechanism
GovernMental Timestamp depen- Timestamp of block is changed by malicious miner
attack dence
time between requests from different nodes, or per- • Transactional Privacy (Leakage): The use of pub-
haps it will become temporarily unavailable. lic, permissionless blockchains may result in the
lack of transactional privacy – leakage or deano-
Specific vulnerabilities include: nymization. A desired benefit of blockchains was
the promise of anonymity (or pseudonymity).
• Unpredictable state / Transaction-Ordering On public blockchains such as Bitcoin, everyone
Dependence: Variables in an Ethereum Contract can see the balance of an address on the block-
can be unpredictable, especially when multi- chain. Perfect privacy is not possible in a public
ple users invoke the same function at the same blockchain if all transactions are accessible by any
time but there is no ordering specified to execute member of the network. As a result, since there
transactions. is a separation of actual identity of the account/
• Generating Randomness: An attempt by a miner signature owner (KYC) from the digital signature,
to influence the manner in which pseudo-random the claim is that blockchain (Bitcoin) is essential-
numbers are generated such as those in smart ly ‘pseudonymous.’ Data in public blockchains is
contracts, such as to simulate a lottery or rolling of generally visible to the public and may only exist
dice. A common option is for code to use the hash in pseudonymous form and is traceable, for exam-
or timestamp from some future time. Since those ple, the transfers to and from an existing address
numbers in the future cannot be predicted, it is can be seen on many public blockchains. Some
assumed they can be used for generation of ran- solutions (such as account mixing) have been sug-
dom numbers. But since all miners have the same gested.
public view of the blockchain and are responsible • Untrustworthy Data Feeds (Oracles): See section
for generating blocks, they can attempt to influ- on Oracles and issues concerning access to data
ence what will be produced at those times where sources (both to and from) which are external to
data is used for random number generation. 351 the blockchain.
• Time Constraints/Timestamp Dependence: See • Bytecode Vulnerabilities/Ethereum Virtual
also Timejacking above as an example of general Machine (EVM): While Solidity has been widely
blockchain vulnerabilities. called a Turing Complete scripting language, the
Security Aspects of Distributed Ledger Technologies 45