Page 50 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 50
9 ADDITIONAL AREAS OF RISKS AND CONCERN IN DLT USE
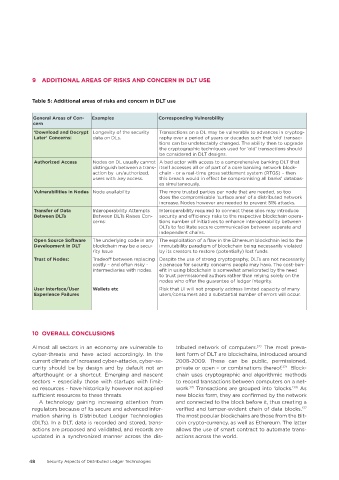
Table 5: Additional areas of risks and concern in DLT use
General Areas of Con- Examples Corresponding Vulnerability
cern
‘Download and Decrypt Longevity of the security Transactions on a DL may be vulnerable to advances in cryptog-
Later’ Concerns: data on DLs. raphy over a period of years or decades such that ‘old’ transac-
tions can be undetectably changed. The ability then to upgrade
the cryptographic techniques used for ‘old’ transactions should
be considered in DLT designs.
Authorized Access Nodes on DL usually cannot A bad actor with access to a comprehensive banking DLT that
distinguish between a trans- itself accesses all or of part of a core banking network block-
action by un/authorized, chain - or a real-time gross settlement system (RTGS) – then
users with .key access. this breach would in effect be compromising all banks’ databas-
es simultaneously.
Vulnerabilities in Nodes Node availability The more trusted parties per node that are needed, so too
does the compromisable ‘surface area' of a distributed network
increase. Nodes however are needed to prevent 51% attacks.
Transfer of Data Interoperability Attempts Interoperability required to connect these silos may introduce
Between DLTs Between DLTs Raises Con- security and efficiency risks to the respective blockchain opera-
cerns: tions number of initiatives to enhance interoperability between
DLTs to facilitate secure communication between separate and
independent chains.
Open Source Software The underlying code in any The exploitation of a flaw in the Ethereum blockchain led to the
Development in DLT blockchain may be a secu- immutability paradigm of blockchain being necessarily violated
rity Issue by its creators to restore (potentially) lost funds.
Trust of Nodes: Tradeoff between replacing Despite the use of strong cryptography, DLTs are not necessarily
costly – and often risky - a panacea for security concerns people may have. The cost-ben-
intermediaries with nodes. efit in using blockchain is somewhat ameliorated by the need
to trust permissioned authors rather than relying solely on the
nodes who offer the guarantee of ledger integrity.
User Interface/User Wallets etc Risk that UI will not properly address limited capacity of many
Experience Failures users/consumers and a substantial number of errors will occur.
10 OVERALL CONCLUSIONS
Almost all sectors in an economy are vulnerable to tributed network of computers. The most preva-
373
cyber-threats and have acted accordingly. In the lent form of DLT are blockchains, introduced around
current climate of increased cyber-attacks, cyber-se- 2008-2009. These can be public, permissioned,
curity should be by design and by default not an private or open – or combinations thereof. Block-
374
afterthought or a shortcut. Emerging and nascent chain uses cryptographic and algorithmic methods
sectors – especially those with startups with limit- to record transactions between computers on a net-
ed resources – have historically however not applied work. Transactions are grouped into ‘blocks.’ As
376
375
sufficient resources to these threats. new blocks form, they are confirmed by the network
A technology gaining increasing attention from and connected to the block before it, thus creating a
regulators because of its secure and advanced infor- verified and tamper-evident chain of data blocks.
377
mation sharing is Distributed Ledger Technologies The most popular blockchains are those from the Bit-
(DLTs). In a DLT, data is recorded and stored, trans- coin crypto-currency, as well as Ethereum. The latter
actions are proposed and validated, and records are allows the use of smart contract to automate trans-
updated in a synchronized manner across the dis- actions across the world.
48 Security Aspects of Distributed Ledger Technologies