Page 37 - Digital Financial Services security assurance framework
P. 37
(continued)
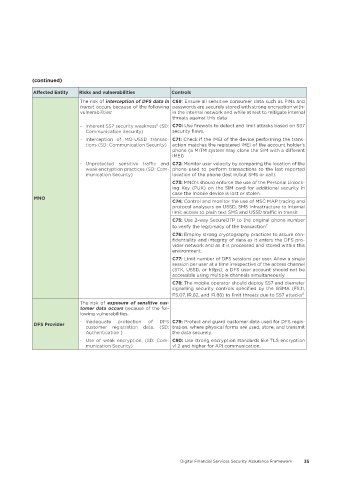
Affected Entity Risks and vulnerabilities Controls
The risk of interception of DFS data in C69: Ensure all sensitive consumer data such as PINs and
transit occurs because of the following passwords are securely stored with strong encryption with-
vulnerabilities: in the internal network and while at rest to mitigate internal
threats against this data.
- Inherent SS7 security weakness (SD: C70: Use firewalls to detect and limit attacks based on SS7
6
Communication Security) security flaws.
- Interception of MO-USSD transac- C71: Check if the IMEI of the device performing the trans-
tions (SD: Communication Security) action matches the registered IMEI of the account holder’s
phone (a MITM system may clone the SIM with a different
IMEI)
- Unprotected sensitive traffic and C72: Monitor user velocity by comparing the location of the
weak encryption practices (SD: Com- phone used to perform transactions to the last reported
munication Security) location of the phone (last in/out SMS or call).
C73: MNO's should enforce the use of the Personal Unlock-
ing Key (PUK) on the SIM card for additional security in
case the mobile device is lost or stolen.
MNO
C74: Control and monitor the use of MSC MAP tracing and
protocol analysers on USSD, SMS infrastructure to internal
limit access to plain text SMS and USSD traffic in transit
C75: Use 2-way SecureOTP to the original phone number
to verify the legitimacy of the transaction 7
C76: Employ strong cryptography practices to assure con-
fidentiality and integrity of data as it enters the DFS pro-
vider network and as it is processed and stored within this
environment.
C77: Limit number of DFS sessions per user. Allow a single
session per user at a time irrespective of the access channel
(STK, USSD, or https); a DFS user account should not be
accessible using multiple channels simultaneously.
C78: The mobile operator should deploy SS7 and diameter
signalling security controls specified by the GSMA (FS.11,
8
FS.07, IR.82, and IR.88) to limit threats due to SS7 attacks
The risk of exposure of sensitive cus-
tomer data occurs because of the fol-
lowing vulnerabilities.
DFS Provider - Inadequate protection of DFS C79: Protect and guard customer data used for DFS regis-
customer registration data. (SD: tration, where physical forms are used, store, and transmit
Authentication ) the data securely.
- Use of weak encryption. (SD: Com- C80: Use strong encryption standards like TLS encryption
munication Security) v1.2 and higher for API communication.
Digital Financial Services Security Assurance Framework 35