Page 38 - Digital Financial Services security assurance framework
P. 38
(continued)
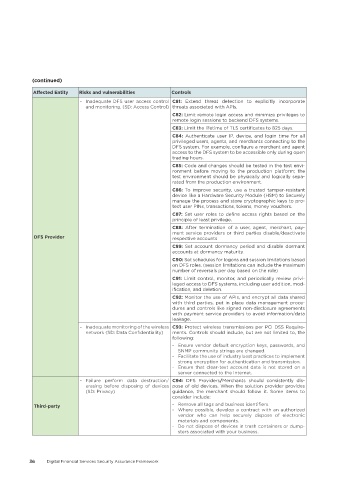
Affected Entity Risks and vulnerabilities Controls
- Inadequate DFS user access control C81: Extend threat detection to explicitly incorporate
and monitoring. (SD: Access Control) threats associated with APIs.
C82: Limit remote login access and minimize privileges to
remote login sessions to backend DFS systems.
C83: Limit the lifetime of TLS certificates to 825 days.
C84: Authenticate user IP, device, and login time for all
privileged users, agents, and merchants connecting to the
DFS system. For example, configure a merchant and agent
access to the DFS system to be accessible only during open
trading hours.
C85: Code and changes should be tested in the test envi-
ronment before moving to the production platform; the
test environment should be physically and logically sepa-
rated from the production environment.
C86: To improve security, use a trusted tamper-resistant
device like a Hardware Security Module (HSM) to Securely
manage the process and store cryptographic keys to pro-
tect user PINs, transactions, tokens, money vouchers.
C87: Set user roles to define access rights based on the
principle of least privilege.
C88: After termination of a user, agent, merchant, pay-
ment service providers or third parties disable/deactivate
DFS Provider respective accounts
C89: Set account dormancy period and disable dormant
accounts at dormancy maturity.
C90: Set schedules for logons and session limitations based
on DFS roles. (session limitations can include the maximum
number of reversals per day based on the role)
C91: Limit control, monitor, and periodically review privi-
leged access to DFS systems, including user addition, mod-
ification, and deletion.
C92: Monitor the use of APIs, and encrypt all data shared
with third parties, put in place data management proce-
dures and controls like signed non-disclosure agreements
with payment service providers to avoid information/data
leakage.
- Inadequate monitoring of the wireless C93: Protect wireless transmissions per PCI DSS Require-
network (SD: Data Confidentiality) ments. Controls should include, but are not limited to, the
following:
- Ensure vendor default encryption keys, passwords, and
SNMP community strings are changed.
- Facilitate the use of industry best practices to implement
strong encryption for authentication and transmission.
- Ensure that clear-text account data is not stored on a
server connected to the Internet.
- Failure perform data destruction/ C94: DFS Providers/Merchants should consistently dis-
erasing before disposing of devices pose of old devices. When the solution provider provides
(SD: Privacy) guidance, the merchant should follow it. Some items to
consider include:
Third-party - Remove all tags and business identifiers.
- Where possible, develop a contract with an authorized
vendor who can help securely dispose of electronic
materials and components.
- Do not dispose of devices in trash containers or dump-
sters associated with your business.
36 Digital Financial Services Security Assurance Framework