Page 17 - Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions
P. 17
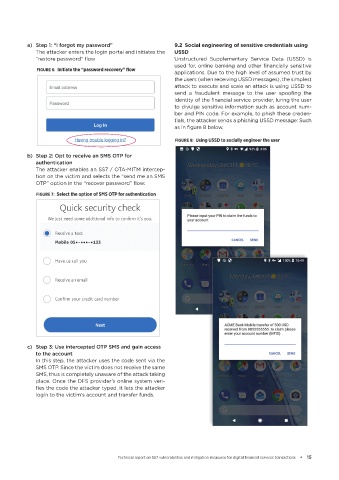
a) Step 1: “I forgot my password” 9.2 Social engineering of sensitive credentials using
The attacker enters the login portal and initiates the USSD
“restore password” flow Unstructured Supplementary Service Data (USSD) is
used for, online banking and other financially sensitive
FIGURE 6: Initiate the “password recovery” flow
applications. Due to the high level of assumed trust by
the users (when receiving USSD messages), the simplest
attack to execute and scale an attack is using USSD to
send a fraudulent message to the user spoofing the
identity of the financial service provider, luring the user
to divulge sensitive information such as account num-
ber and PIN code. For example, to phish these creden-
tials, the attacker sends a phishing USSD message: Such
as in figure 8 below.
FIGURE 8: Using USSD to socially engineer the user
b) Step 2: Opt to receive an SMS OTP for
authentication
The attacker enables an SS7 / OTA-MITM intercep-
tion on the victim and selects the “send me an SMS
OTP” option in the “recover password” flow:
FIGURE 7: Select the option of SMS OTP for authentication
c) Step 3: Use intercepted OTP SMS and gain access
to the account
In this step, the attacker uses the code sent via the
SMS OTP. Since the victim does not receive the same
SMS, thus is completely unaware of the attack taking
place. Once the DFS provider’s online system veri-
fies the code the attacker typed, it lets the attacker
login to the victim’s account and transfer funds.
Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions • 15