Page 16 - Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions
P. 16
8 THE CELLULAR ATTACK KILL CHAIN 9 EXAMPLES OF ATTACKS ON DFS
INFRASTRUCTURE
In order to gain access to sensitive data such as bank-
ing credentials and execute attacks such as online 9.1 SMS OTP interception
account-takeover (ATO) the attacker needs to obtain SMS One Time Password (OTP) is the most popular
information essential to performing the attacks. Table 2 method today for identification strengthening of
below illustrates how an attacker can obtain the infor- authentication processes. The vast majority of DFS pro-
mation required to execute every step in the kill chain by viders use SMS OTP today worldwide. Using SS7 or
leveraging the cellular attacks surfaces: Over-The-Air Man-In-The-Middle (OTA-MITM), SMS
interception, An OTPs obtained from the intercepted
SMS can be used maliciously to gain unlawful access to
users’ accounts. An attacker can use the intercepted
OTP to recover passwords / PIN codes to accounts or
combined with a USSD attack (described below) switch
the phone number associated to an account. Here is an
example of OTP interception and use for unlawful access
to an online account:
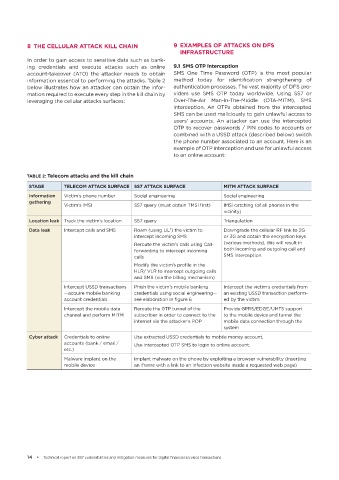
TABLE 2: Telecom attacks and the kill chain
STAGE TELECOM ATTACK SURFACE SS7 ATTACK SURFACE MITM ATTACK SURFACE
Information Victim’s phone number Social engineering Social engineering
gathering
Victim’s IMSI SS7 query (must obtain TMSI first) IMSI catching (of all phones in the
vicinity)
Location leak Track the victim’s location SS7 query Triangulation
Data leak Intercept calls and SMS Roam (using UL ) the victim to Downgrade the cellular RF link to 2G
7
intercept incoming SMS or 3G and obtain the encryption keys
Reroute the victim’s calls using Call- (various methods), this will result in
forwarding to intercept incoming both incoming and outgoing call and
calls SMS interception.
Modify the victim’s profile in the
HLR/ VLR to intercept outgoing calls
and SMS (via the billing mechanism)
Intercept USSD transactions Phish the victim’s mobile banking Intercept the victim’s credentials from
—acquire mobile banking credentials using social engineering— an existing USSD transaction perform-
account credentials see elaboration in figure 6 ed by the victim
Intercept the mobile data Reroute the GTP tunnel of the Provide GPRS/EDGE/UMTS support
channel and perform MITM subscriber in order to connect to the to the mobile device and tunnel the
internet via the attacker’s POP mobile data connection through the
system
Cyber attack Credentials to online Use extracted USSD credentials to mobile money account.
accounts (bank / email / Use intercepted OTP SMS to login to online account.
etc.)
Malware implant on the Implant malware on the phone by exploiting a browser vulnerability (inserting
mobile device an iframe with a link to an infection website inside a requested web page)
14 • Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions