Page 13 - Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions
P. 13
4 COMMON TYPES OF TELECOM ATTACKS
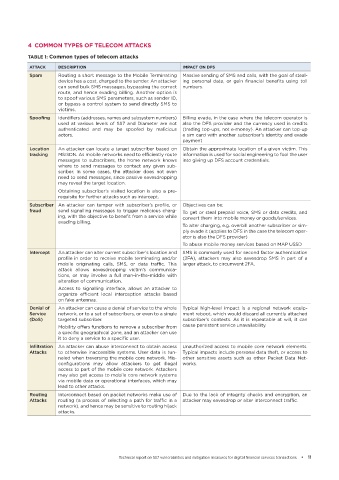
TABLE 1: Common types of telecom attacks
ATTACK DESCRIPTION IMPACT ON DFS
Spam Routing a short message to the Mobile Terminating Massive sending of SMS and calls, with the goal of steal-
device has a cost, charged to the sender. An attacker ing personal data, or gain financial benefits using toll
can send bulk SMS messages, bypassing the correct numbers.
route, and hence evading billing. Another option is
to spoof various SMS parameters, such as sender ID,
or bypass a control system to send directly SMS to
victims.
Spoofing Identifiers (addresses, names and subsystem numbers) Billing evade, in the case where the telecom operator is
used at various levels of SS7 and Diameter are not also the DFS provider and the currency used in credits
authenticated and may be spoofed by malicious (trading top-ups, not e-money). An attacker can top-up
actors. a sim card with another subscriber’s identity and evade
payment
Location An attacker can locate a target subscriber based on Obtain the approximate location of a given victim. This
tracking MSISDN. As mobile networks need to efficiently route information is used for social engineering to fool the user
messages to subscribers, the home network knows into giving up DFS account credentials.
where to send messages to contact any given sub-
scriber. In some cases, the attacker does not even
need to send messages, since passive eavesdropping
may reveal the target location.
Obtaining subscriber’s visited location is also a pre-
requisite for further attacks such as intercept.
Subscriber An attacker can tamper with subscriber’s profile, or Objectives can be:
fraud send signalling messages to trigger malicious charg- To get or steal prepaid voice, SMS or data credits, and
ing, with the objective to benefit from a service while convert them into mobile money or goods/services.
evading billing.
To alter charging, e.g. overbill another subscriber or sim-
ply evade it (applies to DFS in the case the telecom oper-
ator is also the DFS provider)
To abuse mobile money services based on MAP USSD
Intercept An attacker can alter current subscriber’s location and SMS is commonly used for second factor authentication
profile in order to receive mobile terminating and/or (2FA), attackers may also eavesdrop SMS in part of a
mobile originating calls, SMS, or data traffic. This larger attack, to circumvent 2FA.
attack allows eavesdropping victim’s communica-
tions, or may involve a full man-in-the-middle with
alteration of communication.
Access to signalling interface, allows an attacker to
organize efficient local interception attacks based
on fake antennas.
Denial of An attacker can cause a denial of service to the whole Typical high-level impact is a regional network equip-
Service network, or to a set of subscribers, or even to a single ment reboot, which would discard all currently attached
(DoS) targeted subscriber. subscriber’s contexts. As it is repeatable at will, it can
Mobility offers functions to remove a subscriber from cause persistent service unavailability.
a specific geographical zone, and an attacker can use
it to deny a service to a specific user.
Infiltration An attacker can abuse interconnect to obtain access Unauthorized access to mobile core network elements.
Attacks to otherwise inaccessible systems. User data is tun- Typical impacts include personal data theft, or access to
neled when traversing the mobile core network. Mis- other sensitive assets such as other Packet Data Net-
configurations may allow attackers to get illegal works.
access to part of the mobile core network. Attackers
may also get access to mobile core network systems
via mobile data or operational interfaces, which may
lead to other attacks.
Routing Interconnect based on packet networks make use of Due to the lack of integrity checks and encryption, an
Attacks routing (a process of selecting a path for traffic in a attacker may eavesdrop or alter interconnect traffic.
network), and hence may be sensitive to routing hijack
attacks.
Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions • 11