Page 20 - Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions
P. 20
12 MITIGATION STRATEGIES FOR DFS above. Here are some examples of mitigation strategies
PROVIDERS that can be used requiring SS7 connectivity, but not
requiring any investment from the mobile operator.
The first and foremost the DFS provider can do to
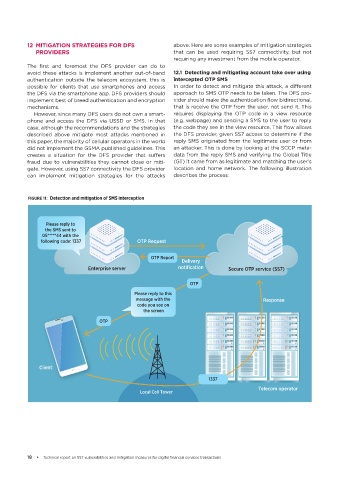
avoid these attacks is implement another out-of-band 12.1 Detecting and mitigating account take over using
authentication outside the telecom ecosystem, this is intercepted OTP SMS
possible for clients that use smartphones and access In order to detect and mitigate this attack, a different
the DFS via the smartphone app. DFS providers should approach to SMS OTP needs to be taken. The DFS pro-
implement best of breed authentication and encryption vider should make the authentication flow bidirectional,
mechanisms. that is receive the OTP from the user, not send it. This
However, since many DFS users do not own a smart- requires displaying the OTP code in a view resource
phone and access the DFS via USSD or SMS. In that (e.g. webpage) and sending a SMS to the user to reply
case, although the recommendations and the strategies the code they see in the view resource. This flow allows
described above mitigate most attacks mentioned in the DFS provider, given SS7 access to determine if the
this paper, the majority of cellular operators in the world reply SMS originated from the legitimate user or from
did not implement the GSMA published guidelines. This an attacker. This is done by looking at the SCCP meta-
creates a situation for the DFS provider that suffers data from the reply SMS and verifying the Global Title
fraud due to vulnerabilities they cannot close or miti- (GT) it came from as legitimate and matching the user’s
gate. However, using SS7 connectivity the DFS provider location and home network. The following illustration
can implement mitigation strategies for the attacks describes the process:
FIGURE 11: Detection and mitigation of SMS interception
Please reply to
the SMS sent to
05*****44 with the
following code: 1337 OTP Request
OTP Report
Delivery
Enterprise server notification Secure OTP service (SS7)
OTP
Please reply to this
message with the Response
code you see on
the screen
OTP
Client
Client
1337
Telecom operator
Local Cell Tower
18 • Technical report on SS7 vulnerabilities and mitigation measures for digital financial services transactions