Page 249 - Big data - Concept and application for telecommunications
P. 249
Big data - Concept and application for telecommunications 5
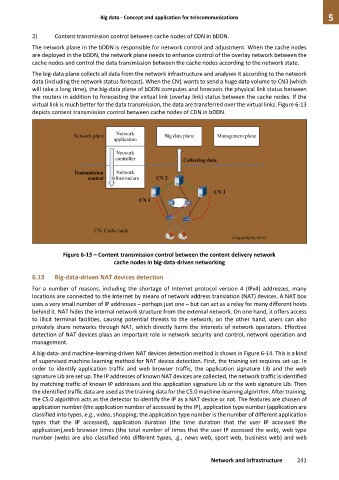
2) Content transmission control between cache nodes of CDN in bDDN.
The network plane in the bDDN is responsible for network control and adjustment. When the cache nodes
are deployed in the bDDN, the network plane needs to enhance control of the overlay network between the
cache nodes and control the data transmission between the cache nodes according to the network state.
The big-data plane collects all data from the network infrastructure and analyses it according to the network
data (including the network status forecast). When the CN1 wants to send a huge data volume to CN3 (which
will take a long time), the big-data plane of bDDN computes and forecasts the physical link status between
the routers in addition to forecasting the virtual link (overlay link) status between the cache nodes. If the
virtual link is much better for the data transmission, the data are transferred over the virtual links. Figure 6-13
depicts content transmission control between cache nodes of CDN in bDDN.
Figure 6-13 – Content transmission control between the content delivery network
cache nodes in big-data-driven networking
6.13 Big-data-driven NAT devices detection
For a number of reasons, including the shortage of Internet protocol version 4 (IPv4) addresses, many
locations are connected to the Internet by means of network address translation (NAT) devices. A NAT box
uses a very small number of IP addresses – perhaps just one – but can act as a relay for many different hosts
behind it. NAT hides the internal network structure from the external network. On one hand, it offers access
to illicit terminal facilities, causing potential threats to the network; on the other hand, users can also
privately share networks through NAT, which directly harm the interests of network operators. Effective
detection of NAT devices plays an important role in network security and control, network operation and
management.
A big-data- and machine-learning-driven NAT devices detection method is shown in Figure 6-14. This is a kind
of supervised machine-learning method for NAT device detection. First, the training set requires set-up. In
order to identify application traffic and web browser traffic, the application signature Lib and the web
signature Lib are set up. The IP addresses of known NAT devices are collected, the network traffic is identified
by matching traffic of known IP addresses and the application signature Lib or the web signature Lib. Then
the identified traffic data are used as the training data for the C5.0 machine-learning algorithm. After training,
the C5.0 algorithm acts as the detector to identify the IP as a NAT device or not. The features are chosen of
application number (the application number of accessed by the IP), application type number (application are
classified into types, e.g., video, shopping; the application type number is the number of different application
types that the IP accessed), application duration (the time duration that the user IP accessed the
application),web browser times (the total number of times that the user IP accessed the web), web type
number (webs are also classified into different types, .g., news web, sport web, business web) and web
Network and infrastructure 241