Page 48 - Trust in ICT 2017
P. 48
1 Trust in ICT
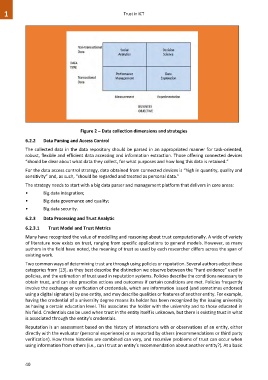
Figure 2 – Data collection dimensions and strategies
6.2.2 Data Parsing and Access Control
The collected data in the data repository should be parsed in an appropriated manner for task-oriented,
robust, flexible and efficient data accessing and information extraction. Those offering connected devices
“should be clear about what data they collect, for what purposes and how long this data is retained.”
For the data access control strategy, data obtained from connected devices is “high in quantity, quality and
sensitivity” and, as such, “should be regarded and treated as personal data.”
The strategy needs to start with a big data parser and management platform that delivers in core areas:
• Big data integration;
• Big data governance and quality;
• Big data security.
6.2.3 Data Processing and Trust Analytic
6.2.3.1 Trust Model and Trust Metrics
Many have recognized the value of modelling and reasoning about trust computationally. A wide of variety
of literature now exists on trust, ranging from specific applications to general models. However, as many
authors in the field have noted, the meaning of trust as used by each researcher differs across the span of
existing work.
Two common ways of determining trust are through using policies or reputation. Several authors adopt these
categories from [13], as they best describe the distinction we observe between the “hard evidence” used in
policies, and the estimation of trust used in reputation systems. Policies describe the conditions necessary to
obtain trust, and can also prescribe actions and outcomes if certain conditions are met. Policies frequently
involve the exchange or verification of credentials, which are information issued (and sometimes endorsed
using a digital signature) by one entity, and may describe qualities or features of another entity. For example,
having the credential of a university degree means its holder has been recognized by the issuing university
as having a certain education level. This associates the holder with the university and to those educated in
his field. Credentials can be used when trust in the entity itself is unknown, but there is existing trust in what
is associated through the entity’s credentials.
Reputation is an assessment based on the history of interactions with or observations of an entity, either
directly with the evaluator (personal experience) or as reported by others (recommendations or third party
verification). How these histories are combined can vary, and recursive problems of trust can occur when
using information from others (i.e., can I trust an entity’s recommendation about another entity?). At a basic
40