Page 43 - Trust in ICT 2017
P. 43
Trust in ICT 1
5.2.11.3 Analysis
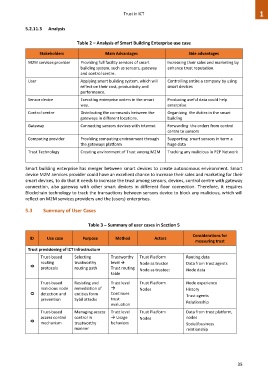
Table 2 – Analysis of Smart Building Enterprise use case
Stakeholders Main Advantages Side advantages
M2M services provider Providing full facility services of smart Increasing their sales and marketing by
building system, such as sensors, gateway enhance trust reputation.
and control centre.
User Applying smart building system, which will Controlling entire a company by using
reflect on their cost, productivity and smart devices
performance.
Sensor device Executing enterprise orders in the smart Producing useful data could help
way. enterprise
Control centre Distributing the commands between the Organizing the duties in the smart
gateways in different locations. building
Gateway Connecting sensors devices with internet Forwarding the orders from control
centre to sensors
Computing provider Providing computing environment through Supporting smart sensors in term a
the gateways platform huge data
Trust Technology Creating environment of Trust among M2M Tracking any malicious in P2P Network
Smart building enterprise has merger between smart devices to create autonomous environment. Smart
device M2M services provider could have an excellent chance to increase their sales and marketing for their
smart devices, to do that it needs to increase the trust among sensors, devices, control centre with gateway
connection, also gateway with other smart devices in different floor connection. Therefore, it requires
Blockchain technology to track the transactions between sensors device to block any malicious, which will
reflect on M2M services providers and the (users) enterprises.
5.3 Summary of User Cases
Table 3 – Summary of user cases in Section 5
Considerations for
ID Use case Purpose Method Actors
measuring trust
Trust provisioning of ICT infrastructure
Trust-based Selecting Trustworthy Trust Platform Routing data
routing trustworthy level Node as trustor Data from trust agents
0 protocols routing path Trust routing Node as trustee: Node data
table
Trust-based Resisting and Trust level Trust Platform Node experience
malicious node remediation of Nodes History
0 detection and entities form Continues Trust agents
prevention Sybil attacks trust
evaluation Relationship
Trust-based Managing access Trust level Trust Platform Data from trust platform,
access control control in Usage Nodes nodes
0
mechanism trustworthy behaviors Social/business
manner relationship
35