Page 45 - Trust in ICT 2017
P. 45
Trust in ICT 1
Considerations for
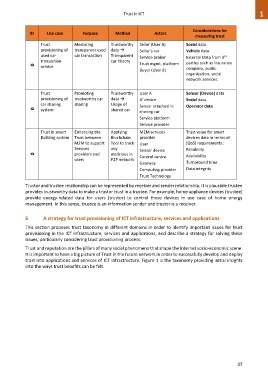
ID Use case Purpose Method Actors
measuring trust
Trust Mediating Trustworthy Seller (User A) Social data
provisioning of transparent used data Seller’s car Vehicle data
used car car transaction Transparent rd
Service broker External Data from 3
transaction car history
0 service Trust mgmt. platform parties such as insurance
Buyer (User B) company, public
organization, social
network services.
Trust Promoting Trustworthy User A Sensor (Device) data
provisioning of trustworthy car data A’ device Social data
car sharing sharing Usage of Sensor attached in Operator data
0 system shared car
sharing car
Service platform
Service provider
Trust in smart Enhancing the Applying M2M services Trust value for smart
Building system Trust between Blochchain provider devices data in terms of
M2M to support Tool to track User (QoS) requirements :
Services any Sensor device Reliability
0 providers and malicious in
Control centre Availability
users P2P network
Gateway Turnaround time
Computing provider Data integrity
Trust Technology
Trustor and trustee relationship can be represented by receiver and sender relationship. It is plausible trustee
provides trustworthy data to make a trustor trust in a trustee. For example, home appliance devices (trustee)
provide energy-related data for users (trustor) to control these devices in use case of home energy
management. In this sense, trustee is an information sender and trustor is a receiver.
6 A strategy for trust provisioning of ICT infrastructure, services and applications
This section proposes trust taxonomy in different domains in order to identify important issues for trust
provisioning in the ICT infrastructure, services and applications, and describe a strategy for solving these
issues, particularly considering trust provisioning process.
Trust and reputation are the pillars of many social phenomena that shape the Internet socio-economic scene.
It is important to have a big picture of Trust in the future network in order to successfully develop and deploy
trust into applications and services of ICT infrastructure. Figure 1 is the taxonomy providing initial insights
into the ways trust benefits can be felt.
37