Page 44 - Trust in ICT 2017
P. 44
1 Trust in ICT
Considerations for
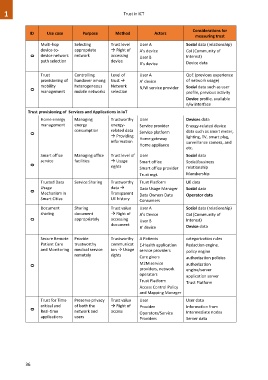
ID Use case Purpose Method Actors
measuring trust
Multi-hop Selecting Trust level User A Social data (relationship)
device-to- appropriate Right of A’s device CoI (Community of
0 device network network accessing User B Interest)
path selection device
B’s device Device data
Trust Controlling Level of User A QoE (previous experience
provisioning of handover among trust A’ device of network usage)
mobility heterogeneous Network Social data such as user
0 N/W service provider
management mobile networks selection profile, previous activity
Device profile, available
n/w interface
Trust provisioning of Services and Applications in IoT
Home energy Managing Trustworthy User Devices data
management energy energy- Service provider Energy-related device
consumption related data data such as smart meter,
0 Service platform
Providing lighting, TV, smart plug,
Home gateway
information surveillance camera, and
Home appliance
etc.
Smart office Managing office Trust level of User Social data
service facilities Usage Smart office Social/business
0 rights Smart office provider relationship
Trust mgt. Membership
Trusted Data Service Sharing Trustworthy Trust Platform UE data
Usage data Data Usage Manager Social data
0
Mechanism in Transparent
Data Owners Data Operator data
Smart Cities UE history
Consumers
Document Sharing Trust value User A Social data (relationship)
sharing document Right of A’s Device CoI (Community of
0 appropriately accessing User B Interest)
document
B’ device Device data
Secure Remote Provide Trustworthy A Patients categorization rules
Patient Care trustworthy communicat E-Health application Redaction engine.
and Monitoring medical service ion Usage service providers
policy engine
remotely rights
Care givers authorization policies
0 M2M service authorization
providers, network engine/server
operators application server
Trust Platform
Trust Platform
Access Control Policy
and Mapping Manager
Trust for Time Preserve privacy Trust value User User data
critical and of both the Right of Provider Information from
0
Real-time network and access Operators/Service Intermediate nodes
applications users Providers Server data
36