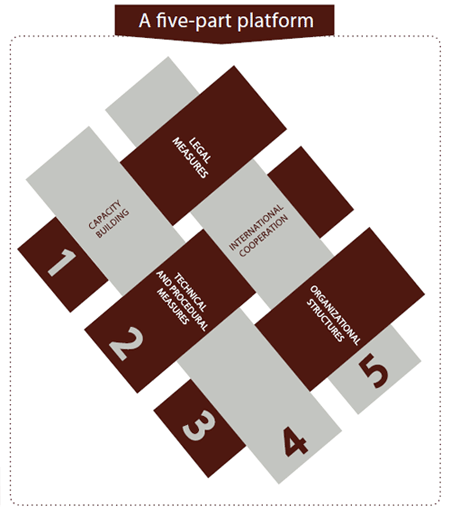
Council 2019 instructed the Secretary-General, in parallel, to submit to the next Council session (1) a report explaining how the ITU is currently utilizing the Global Cybersecurity Agenda (GCA) framework and (2) with the involvement of Member States, appropriate guidelines developed for utilization of the GCA by the ITU for Council's consideration and approval (C19/117, C19/58).
Learn more