Page 236 - Kaleidoscope Academic Conference Proceedings 2024
P. 236
2024 ITU Kaleidoscope Academic Conference
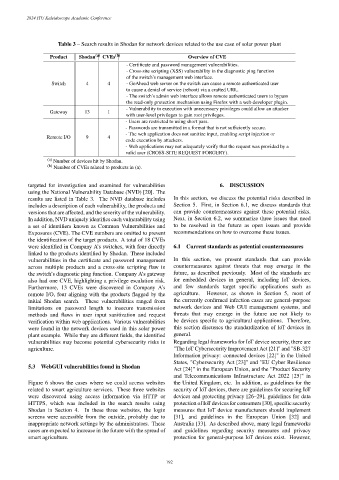
Table 3 – Search results in Shodan for network devices related to the use case of solar power plant
Product Shodan (a) CVEs (b) Overview of CVE
- Certificate and password management vulnerabilities.
- Cross-site scripting (XSS) vulnerability in the diagnostic ping function
of the switch’s management web interface.
Switch 4 4 - GoAhead web server on the switch can cause a remote authenticated user
to cause a denial of service (reboot) via a crafted URL.
- The switch’s admin web interface allows remote authenticated users to bypass
the read-only protection mechanism using Firefox with a web developer plugin.
- Vulnerability to execution with unnecessary privileges could allow an attacker
Gateway 13 1
with user-level privileges to gain root privileges.
- Users are restricted to using short pass.
- Passwords are transmitted in a format that is not sufficiently secure.
- The web application does not sanitize input, enabling script injection or
Remote I/O 9 4
code execution by attackers.
- Web applications may not adequately verify that the request was provided by a
valid user (CROSS-SITE REQUEST FORGERY).
(a) Number of devices hit by Shodan.
(b) Number of CVEs related to products in (a).
targeted for investigation and examined for vulnerabilities 6. DISCUSSION
using the National Vulnerability Database (NVD) [20]. The
results are listed in Table 3. The NVD database includes In this section, we discuss the potential risks described in
includes a description of each vulnerability, the products and Section 5. First, in Section 6.1, we discuss standards that
versions that are affected, and the severity of the vulnerability. can provide countermeasures against these potential risks.
In addition, NVD uniquely identifies each vulnerability using Next, in Section 6.2, we summarize three issues that need
a set of identifiers known as Common Vulnerabilities and to be resolved in the future as open issues and provide
Exposures (CVE). The CVE numbers are omitted to prevent recommendations on how to overcome these issues.
the identification of the target products. A total of 18 CVEs
were identified in Company A’s switches, with four directly 6.1 Current standards as potential countermeasures
linked to the products identified by Shodan. These included
vulnerabilities in the certificate and password management In this section, we present standards that can provide
across multiple products and a cross-site scripting flaw in countermeasures against threats that may emerge in the
the switch’s diagnostic ping function. Company A’s gateway future, as described previously. Most of the standards are
also had one CVE, highlighting a privilege escalation risk. for embedded devices in general, including IoT devices,
Furthermore, 13 CVEs were discovered in Company A’s and few standards target specific applications such as
remote I/O, four aligning with the products flagged by the agriculture. However, as shown in Section 5, most of
initial Shodan search. These vulnerabilities ranged from the currently confirmed infection cases are general-purpose
limitations on password length to insecure transmission network devices and Web GUI management systems, and
methods and flaws in user input sanitization and request threats that may emerge in the future are not likely to
verification within web applications. Various vulnerabilities be devices specific to agricultural applications. Therefore,
were found in the network devices used in this solar power this section discusses the standardization of IoT devices in
plant example. While they are different fields, the identified general.
vulnerabilities may become potential cybersecurity risks in Regarding legal frameworks for IoT device security, there are
agriculture. "The IoT Cybersecurity Improvement Act [21]" and "SB-327
Information privacy: connected devices [22]" in the United
States, "Cybersecurity Act [23]" and "EU Cyber Resilience
5.3 WebGUI vulnerabilities found in Shodan
Act [24]" in the European Union, and the "Product Security
and Telecommunications Infrastructure Act 2022 [25]" in
Figure 6 shows the cases where we could access websites the United Kingdom, etc. In addition, as guidelines for the
related to smart agriculture services. These three websites security of IoT devices, there are guidelines for securing IoT
were discovered using access information via HTTP or devices and protecting privacy [26–29], guidelines for data
HTTPS, which was included in the search results using protection of IoT devices for consumers [30], specific security
Shodan in Section 4. In these three websites, the login measures that IoT device manufacturers should implement
screens were accessible from the outside, probably due to [31], and guidelines in the European Union [32] and
inappropriate network settings by the administrators. These Australia [33]. As described above, many legal frameworks
cases are expected to increase in the future with the spread of and guidelines regarding security measures and privacy
smart agriculture. protection for general-purpose IoT devices exist. However,
– 192 –