Page 81 - ITU Journal Future and evolving technologies Volume 2 (2021), Issue 6 – Wireless communication systems in beyond 5G era
P. 81
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 6
′′
(P1 ) ∶ max
, , , , , ,
log( ) + log( , , , ) + log( ) + log( , , , )
, , , , , ,
, , , , , ,
∈ℐ ∈ ∈{ℰ∪ℳ∪ℛ} ∈ℐ ∈ℱ ∈{ℰ∪ℳ}
+ log( ) + log( , , , ) + log( )
, , , , , ,
, , , , , ,
∈ℐ ∈ ∈{ℰ∪ℳ} ∈ℐ ∈ ∈ ℱ ∈{ℰ∪ℳ}
+ log( , , , ) (27)
∈ℐ ∈ ∈ ℱ ∈{ℰ∪ℳ}
7.2 SP‑MVNO resource allocation SP
It is important to note that , is pivotal in slicing the re‑ Pa s
source in (27). Solving , entails the SP‑MVNO hierar‑ Ded a es
Resou es
chical layer described in Section 4. For a simple case of a
single resource (i.e., bandwidth) and from Section 4, , M NO
is given as:
Ded a es Pa s
, = ℬ , , , ∈ , ∈ ℐ (28) Resou es
∈ℋ InP
where ℬ is the overall bandwidth size of InP . Moreover,
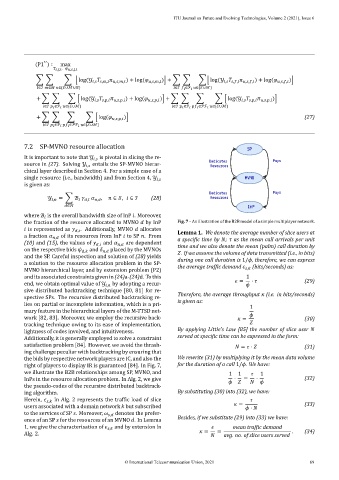
the fraction of the resource allocated to MVNO by InP Fig. 7 – An illustration of the B2B model of a simple multiplayer network.
is represented as . Additionally, MVNO allocates Lemma 1. We denote the average number of slice users at
,
a fraction , of its resources from InP to SP . From a speci ic time by ; as the mean call arrivals per unit
(10) and (15), the values of , and , are dependent time and we also denote the mean (palm) call duration by
on the respective bids , and , placed by the MVNOs . If we assume the volume of data transmitted (i.e., in bits)
and the SP. Careful inspection and solution of (28) yields during one call duration is 1/ , therefore, we can express
a solution to the resource allocation problem in the SP‑ the average traf ic demand (bits/seconds) as:
MVNO hierarchical layer, and by extension problem (P2) ,
and its associated constraints given in (24)a‑(24)d. To this 1
end, we obtain optimal value of , by adopting a recur‑ = ⋅ (29)
sive distributed backtracking technique [80, 81] for re‑
Therefore, the average throughput (i.e. in bits/seconds)
spective SPs. The recursive distributed backtracking re‑ is given as:
lies on partial or incomplete information, which is a pri‑ 1
mary feature in the hierarchical layers of the M‑TTSD net‑
work [82, 83]. Moreover, we employ the recursive back‑ = (30)
tracking technique owing to its ease of implementation,
lightness of codes involved, and intuitiveness. By applying Little’s Law [85] the number of slice user
Additionally, it is generally employed to solve a constraint served at speci ic time can be expressed in the form:
satisfaction problem [84]. However, we avoid the thrash‑ = ⋅ (31)
ing challenge peculiar with backtracking by ensuring that
the bids by respective network players are IC, and also the We rewrite (31) by multiplying it by the mean data volume
right of players to display IR is guaranteed [84]. In Fig. 7, for the duration of a call 1/ . We have:
we illustrate the B2B relationships among SP, MVNO, and 1 1 1
⋅
⋅
InPs in the resource allocation problem. In Alg. 2, we give = (32)
the pseudo‑codes of the recursive distributed backtrack‑
ing algorithm. By substituting (30) into (32), we have:
Herein, , in Alg. 2 represents the traf ic load of slice
users associated with a domain network but subscribed = ⋅ (33)
to the services of SP . Moreover, , denotes the prefer‑
ence of an SP for the resources of an MVNO . In Lemma Besides, if we substitute (29) into (33) we have:
1, we give the characterisation of , and by extension in mean traf ic demand
Alg. 2. = = avg. no. of slice users served . (34)
© International Telecommunication Union, 2021 69