Page 60 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 60
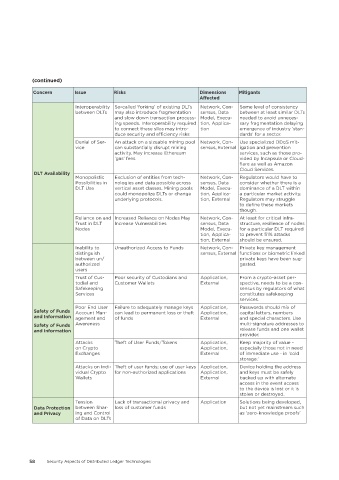
(continued)
Concern Issue Risks Dimensions Mitigants
Affected
Interoperability So-called ‘forking’ of existing DLTs Network, Con- Some level of consistency
between DLTs may also introduce fragmentation sensus, Data between at least similar DLTs
and slow down transaction process- Model, Execu- needed to avoid unneces-
ing speeds. Interoperability required tion, Applica- sary fragmentation delaying
to connect these silos may intro- tion emergence of industry ‘stan-
duce security and efficiency risks dards’ for a sector.
Denial of Ser- An attack on a sizeable mining pool Network, Con- Use specialized DDoS mit-
vice can substantially disrupt mining sensus, External igation and prevention
activity. May increase Ethereum services, such as those pro-
‘gas’ fees. vided by Incapsula or Cloud-
flare as well as Amazon
Cloud Services.
DLT Availability
Monopolistic Exclusion of entities from tech- Network, Con- Regulators would have to
Possibilities in nologies and data possible across sensus, Data consider whether there is a
DLT Use vertical asset classes. Mining pools Model, Execu- dominance of a DLT within
could monopolize DLTs or change tion, Applica- a particular market activity.
underlying protocols. tion, External Regulators may struggle
to define these markets
though.
Reliance on and Increased Reliance on Nodes May Network, Con- At least for critical infra-
Trust in DLT Increase Vulnerabilities sensus, Data structure, resilience of nodes
Nodes Model, Execu- for a particular DLT required
tion, Applica- to prevent 51% attacks
tion, External should be ensured.
Inability to Unauthorized Access to Funds Network, Con- Private key management
distinguish sensus, External functions or biometric linked
between un/ private keys have been sug-
authorized gested.
users
Trust of Cus- Poor security of Custodians and Application, From a crypto-asset per-
todial and Customer Wallets External spective, needs to be a con-
Safekeeping sensus by regulators of what
Services constitutes safekeeping
services.
Poor End User Failure to adequately manage keys Application, Passwords should mix of
Safety of Funds Account Man- can lead to permanent loss or theft Application, capital letters, numbers
and Information agement and of funds External and special characters. Use
Safety of Funds Awareness multi-signature addresses to
and Information release funds and one wallet
provider.
Attacks Theft of User Funds/Tokens Application, Keep majority of value -
on Crypto Application, especially those not in need
Exchanges External of immediate use - in ‘cold
storage.’
Attacks on Indi- Theft of user funds; use of user keys Application, Device holding the address
vidual Crypto for non-authorized applications Application, and keys must be safely
Wallets External backed up with alternate
access in the event access
to the device is lost or it is
stolen or destroyed.
Tension Lack of transactional privacy and Application Solutions being developed,
Data Protection between Shar- loss of customer funds but not yet mainstream such
and Privacy ing and Control as ‘zero-knowledge proofs’
of Data on DLTs
58 Security Aspects of Distributed Ledger Technologies