Page 26 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 26
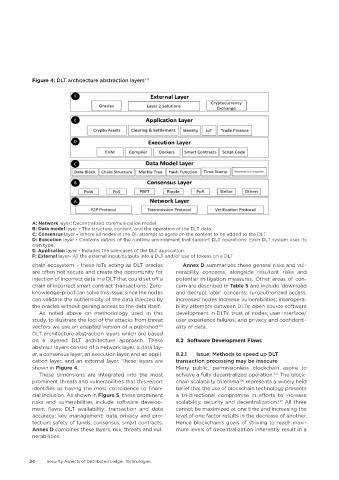
Figure 4: DLT architecture abstraction layers 134
A: Network layer: Decentralized communication model
B: Data model layer - The structure, content, and the operation of the DLT data.
C: Consensus layer - Where all nodes in the DL attempt to agree on the content to be added to the DLT
D: Execution layer - Contains details of the runtime environment that support DLT operations. Each DLT system uses its
own type.
E: Application layer - Includes the use-cases of the DLT application.
F: External layer- All the external input/outputs into a DLT and/or use of tokens on a DLT
chain ecosystem – these IoTs acting as DLT oracles Annex D summarizes these general risks and vul-
are often not secure and create the opportunity for nerability concerns, alongside resultant risks and
injection of incorrect data in a DLT that could set off a potential mitigation measures. Other areas of con-
chain of incorrect smart contract ‘transactions.’ Zero- cern are described in Table 5 and include ‘download
knowledge-proof can solve this issue, since the nodes and decrypt later’ concerns; (un)authorized access;
can validate the authenticity of the data injected by increased nodes increase vulnerabilities; interopera-
the oracles without gaining access to the data itself. bility attempts between DLTs; open source software
As noted above on methodology used in this development in DLTs; trust of nodes; user interface/
study, to illustrate the loci of the attacks from threat user experience failures; and privacy and confidenti-
vectors we use an adapted version of a published ality of data.
133
DLT architecture abstraction layers which are based
on a layered DLT architecture approach. These 8�2 Software Development Flaws
abstract layers consist of a network layer, a data lay-
er, a consensus layer, an execution layer, and an appli- 8.2.1 Issue: Methods to speed up DLT
cation layer, and an external layer. These layers are transaction processing may be insecure
shown in Figure 4� Many public, permissionless blockchain aspire to
These dimensions are integrated into the most achieve a fully decentralized operation. The block-
135
prominent threats and vulnerabilities that this report chain scalability trilemma represents a widely held
136
identifies as having the most coincidence to finan- belief that the use of blockchain technology presents
cial inclusion. As shown in Figure 5, these prominent a tri-directional compromise in efforts to increase
risks and vulnerabilities include software develop- scalability, security and decentralization. All three
137
ment flaws; DLT availability; transaction and data cannot be maximized at one time and increasing the
accuracy; key management; data privacy and pro- level of one factor results in the decrease of another.
tection; safety of funds; consensus; smart contracts. Hence blockchain’s goals of striving to reach maxi-
Annex D combines these layers, risk, threats and vul- mum levels of decentralization inherently result in a
nerabilities.
24 Security Aspects of Distributed Ledger Technologies