Page 25 - FIGI: Security Aspects of Distributed Ledger Technologies
P. 25
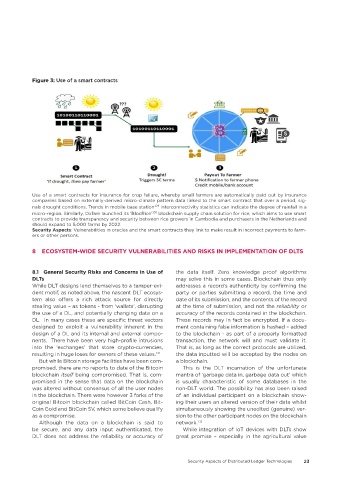
Figure 3: Use of a smart contracts
Use of a smart contracts for insurance for crop failure, whereby small farmers are automatically paid out by insurance
companies based on externally-derived micro-climate pattern data linked to the smart contract that over a period, sig-
nals drought conditions. Trends in mobile base station 129 interconnectivity statistics can indicate the degree of rainfall in a
micro-region. Similarly, Oxfam launched its ‘BlocRice’ 130 blockchain supply chain solution for rice, which aims to use smart
contracts to provide transparency and security between rice growers in Cambodia and purchasers in the Netherlands and
should expand to 5,000 farms by 2022.
Security Aspects: Vulnerabilities in oracles and the smart contracts they link to make result in incorrect payments to farm-
ers or other persons.
8 ECOSYSTEM-WIDE SECURITY VULNERABILITIES AND RISKS IN IMPLEMENTATION OF DLTS
8�1 General Security Risks and Concerns in Use of the data itself. Zero knowledge proof algorithms
DLTs may solve this in some cases. Blockchain thus only
While DLT designs lend themselves to a tamper-evi- addresses a record’s authenticity by confirming the
dent motif, as noted above, the nascent DLT ecosys- party or parties submitting a record, the time and
tem also offers a rich attack source for directly date of its submission, and the contents of the record
stealing value – as tokens - from ‘wallets’, disrupting at the time of submission, and not the reliability or
the use of a DL, and potentially changing data on a accuracy of the records contained in the blockchain.
DL. In many cases these are specific threat vectors These records may in fact be encrypted. If a docu-
designed to exploit a vulnerability inherent in the ment containing false information is hashed – added
design of a DL and its internal and external compo- to the blockchain - as part of a properly formatted
nents. There have been very high-profile intrusions transaction, the network will and must validate it.
into the ‘exchanges’ that store crypto-currencies, That is, as long as the correct protocols are utilized,
resulting in huge loses for owners of these values. 131 the data inputted will be accepted by the nodes on
But while Bitcoin storage facilities have been com- a blockchain.
promised, there are no reports to date of the Bitcoin This is the DLT incarnation of the unfortunate
blockchain itself being compromised. That is, com- mantra of ‘garbage data in, garbage data out’ which
promised in the sense that data on the blockchain is usually characteristic of some databases in the
was altered without consensus of all the user nodes non-DLT world. The possibility has also been raised
in the blockchain. There were however 3 forks of the of an individual participant on a blockchain show-
original Bitcoin blockchain called BitCoin Cash, Bit- ing their users an altered version of their data whilst
Coin Gold and BitCoin SV, which some believe qualify simultaneously showing the unedited (genuine) ver-
as a compromise. sion to the other participant nodes on the blockchain
Although the data on a blockchain is said to network.
132
be secure, and any data input authenticated, the While integration of IoT devices with DLTs show
DLT does not address the reliability or accuracy of great promise – especially in the agricultural value
Security Aspects of Distributed Ledger Technologies 23