Page 37 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 37
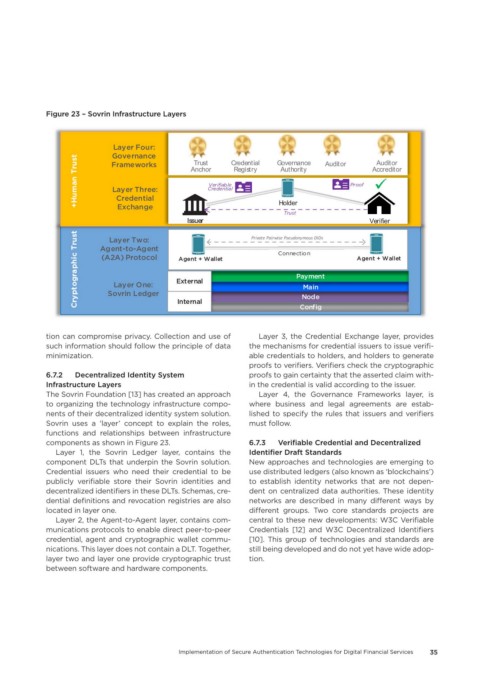
Figure 23 – Sovrin Infrastructure Layers
Layer Four:
Governance
+Human Trust Frameworks Anchor Credential Credential Governance Auditor Proof Accreditor
Auditor
Trust
Registry
Authority
Verifiable
Layer Three:
Credential
$ $
Holder
Exchange
` `
Trust
I Issuerssuer Private Pairwise Pseudonymous DIDs Verifier
Cryptographic Trust Agent-to-Agent External Connection Agent + Wallet
Layer Two:
(A2A) Protocol
Agent + Wallet
Payment
Layer One:
Main
Sovrin Ledger
Node
Internal
Config
tion can compromise privacy. Collection and use of Layer 3, the Credential Exchange layer, provides
such information should follow the principle of data the mechanisms for credential issuers to issue verifi-
minimization. able credentials to holders, and holders to generate
proofs to verifiers. Verifiers check the cryptographic
6.7.2 Decentralized Identity System proofs to gain certainty that the asserted claim with-
Infrastructure Layers in the credential is valid according to the issuer.
The Sovrin Foundation [13] has created an approach Layer 4, the Governance Frameworks layer, is
to organizing the technology infrastructure compo- where business and legal agreements are estab-
nents of their decentralized identity system solution. lished to specify the rules that issuers and verifiers
Sovrin uses a ‘layer’ concept to explain the roles, must follow.
functions and relationships between infrastructure
components as shown in Figure 23. 6.7.3 Verifiable Credential and Decentralized
Layer 1, the Sovrin Ledger layer, contains the Identifier Draft Standards
component DLTs that underpin the Sovrin solution. New approaches and technologies are emerging to
Credential issuers who need their credential to be use distributed ledgers (also known as ‘blockchains’)
publicly verifiable store their Sovrin identities and to establish identity networks that are not depen-
decentralized identifiers in these DLTs. Schemas, cre- dent on centralized data authorities. These identity
dential definitions and revocation registries are also networks are described in many different ways by
located in layer one. different groups. Two core standards projects are
Layer 2, the Agent-to-Agent layer, contains com- central to these new developments: W3C Verifiable
munications protocols to enable direct peer-to-peer Credentials [12] and W3C Decentralized Identifiers
credential, agent and cryptographic wallet commu- [10]. This group of technologies and standards are
nications. This layer does not contain a DLT. Together, still being developed and do not yet have wide adop-
layer two and layer one provide cryptographic trust tion.
between software and hardware components.
Implementation of Secure Authentication Technologies for Digital Financial Services 35