Page 35 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 35
ries, customers etc. without having to store Aad- This type of transformation is warranted today
haar number in their databases while not being through a combination of multi-modal and contextu-
able to merge databases across agencies thus al controls that continuously and accurately protect
enhancing privacy. user identity and privacy even if your online creden-
c) Biometric locking tials are already compromised. Cognitive Continu-
This service is meant to help users protect their ous Authentication™ uses AIML and a combination
biometric details from being misused in one way of multi-modal and contextual controls that con-
or the other. It is worth noting that many agen- tinuously and accurately protect user transactions,
cies require applicants to verify their details using and identity and privacy. Pairing AI with a mixture
the Aadhaar biometric authenticate facility. UIDAI of Machine learning (AIML) can be used in the back-
may enable an Aadhaar number holder to perma- ground, learning the digital behavior of users within
nently lock his biometrics and temporarily unlock context. By taking a holistic approach to how some-
it when needed for biometric authentication. one transacts, AI can determine if a bad actor is try-
All biometric authentication against any such ing to initiate a fraudulent transaction.
locked biometric records shall fail with a “No” Cognitive Continuous Authentication™ starts col-
answer with an appropriate response code. An lection of intelligence pre-authentication, uses a rich
Aadhaar holder shall be allowed to temporari- set of contextual data instead of binary authenti-
ly unlock his/her biometrics for authentication, cation to deliver a new state of the art risk-based
and such temporary unlocking shall not contin- authentication with lower friction for the good
ue beyond the time period specified by UIDAI or actors and then most importantly a post authoriza-
till completion of the authentication transaction, tion continuous authentication that detects transac-
whichever is earlier. tion anomalies leveraging the new controls including
UIDAI can enable Aadhaar holders to remove such the use of AIML.
permanent locks at any point in a secure manner. Figure 21 below shows the users journey in
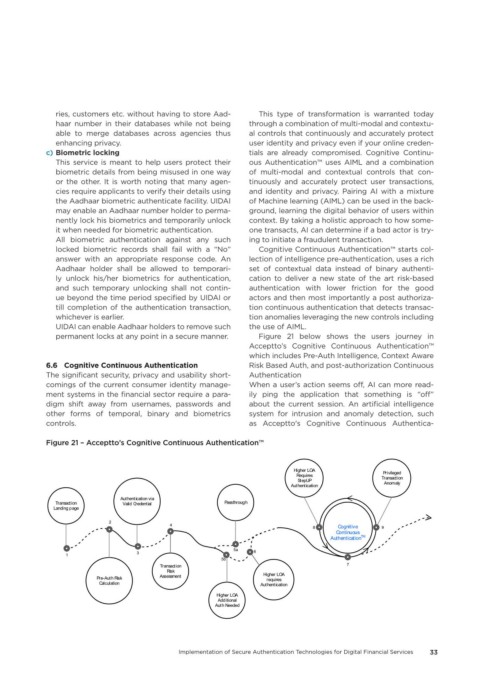
Acceptto’s Cognitive Continuous Authentication™
which includes Pre-Auth Intelligence, Context Aware
6�6 Cognitive Continuous Authentication Risk Based Auth, and post-authorization Continuous
The significant security, privacy and usability short- Authentication
comings of the current consumer identity manage- When a user’s action seems off, AI can more read-
ment systems in the financial sector require a para- ily ping the application that something is “off”
digm shift away from usernames, passwords and about the current session. An artificial intelligence
other forms of temporal, binary and biometrics system for intrusion and anomaly detection, such
controls. as Acceptto's Cognitive Continuous Authentica-
Figure 21 – Acceptto’s Cognitive Continuous Authentication™
Higher LOA Privileged
Requires Transaction
StepUP
Authentication Anomaly
Authentication via
Transaction Valid Credential Passthrough
Landing page
2
4 Cognitive
8 9
Continuous
Authentication TM
5a
3 6
1
5b
Transaction 7
Risk
Assessment Higher LOA
Pre-Auth Risk requires
Calculation Authentication
Higher LOA
Additional
Auth Needed
Implementation of Secure Authentication Technologies for Digital Financial Services 33