Page 41 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 41
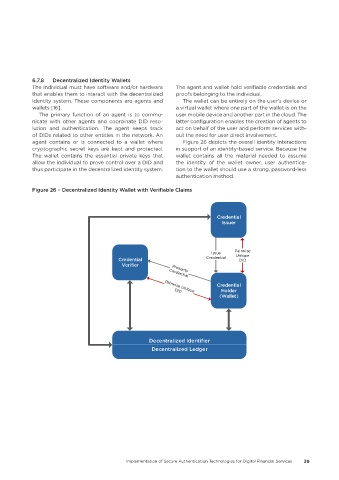
6.7.8 Decentralized Identity Wallets
The individual must have software and/or hardware The agent and wallet hold verifiable credentials and
that enables them to interact with the decentralized proofs belonging to the individual.
identity system. These components are agents and The wallet can be entirely on the user’s device or
wallets [16]. a virtual wallet where one part of the wallet is on the
The primary function of an agent is to commu- user mobile device and another part in the cloud. The
nicate with other agents and coordinate DID reso- latter configuration enables the creation of agents to
lution and authentication. The agent keeps track act on behalf of the user and perform services with-
of DIDs related to other entities in the network. An out the need for user direct involvement.
agent contains or is connected to a wallet where Figure 26 depicts the overall identity interactions
cryptographic secret keys are kept and protected. in support of an identity-based service. Because the
The wallet contains the essential private keys that wallet contains all the material needed to assume
allow the individual to prove control over a DID and the identity of the wallet owner, user authentica-
thus participate in the decentralized identity system. tion to the wallet should use a strong, password-less
authentication method.
Figure 26 – Decentralized Identity Wallet with Verifiable Claims
Credential
Issuer
Pairwise
Issue Unique
Credential Credential DID
Verifier
Credential
Holder
(Wallet)
Decentralized Identifier
Decentralized Ledger
Implementation of Secure Authentication Technologies for Digital Financial Services 39