Page 31 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 31
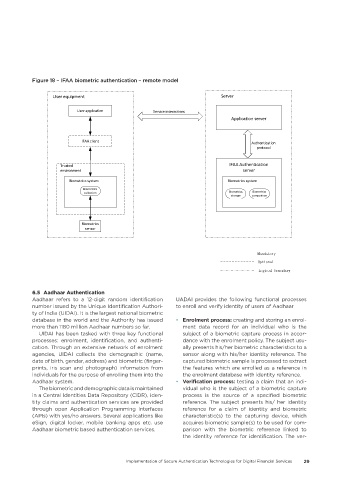
Figure 18 – IFAA biometric authentication – remote model
User equipment Server
User application Service interactions
Application server
IFAA client Authentication
protocol
Trusted IFAA Authentication
environment server
Biometrics system Biometrics system
Biometrics
collection Biometrics Biometrics
storage comparison
Biometrics
sensor
Mandatory
Optional
Logical boundary
6�5 Aadhaar Authentication
Aadhaar refers to a 12-digit random identification UADAI provides the following functional processes
number issued by the Unique Identification Authori- to enroll and verify identity of users of Aadhaar
ty of India (UIDAI). It is the largest national biometric
database in the world and the Authority has issued • Enrolment process: creating and storing an enrol-
more than 1180 million Aadhaar numbers so far. ment data record for an individual who is the
UIDAI has been tasked with three key functional subject of a biometric capture process in accor-
processes: enrolment, identification, and authenti- dance with the enrolment policy. The subject usu-
cation. Through an extensive network of enrolment ally presents his/her biometric characteristics to a
agencies, UIDAI collects the demographic (name, sensor along with his/her identity reference. The
date of birth, gender, address) and biometric (finger- captured biometric sample is processed to extract
prints, iris scan and photograph) information from the features which are enrolled as a reference in
individuals for the purpose of enrolling them into the the enrolment database with identity reference.
Aadhaar system. • Verification process: testing a claim that an indi-
The biometric and demographic data is maintained vidual who is the subject of a biometric capture
in a Central Identities Data Repository (CIDR), iden- process is the source of a specified biometric
tity claims and authentication services are provided reference. The subject presents his/ her identity
through open Application Programming Interfaces reference for a claim of identity and biometric
(APIs) with yes/no answers. Several applications like characteristic(s) to the capturing device, which
eSign, digital locker, mobile banking apps etc. use acquires biometric sample(s) to be used for com-
Aadhaar biometric based authentication services. parison with the biometric reference linked to
the identity reference for identification. The ver-
Implementation of Secure Authentication Technologies for Digital Financial Services 29