Page 29 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 29
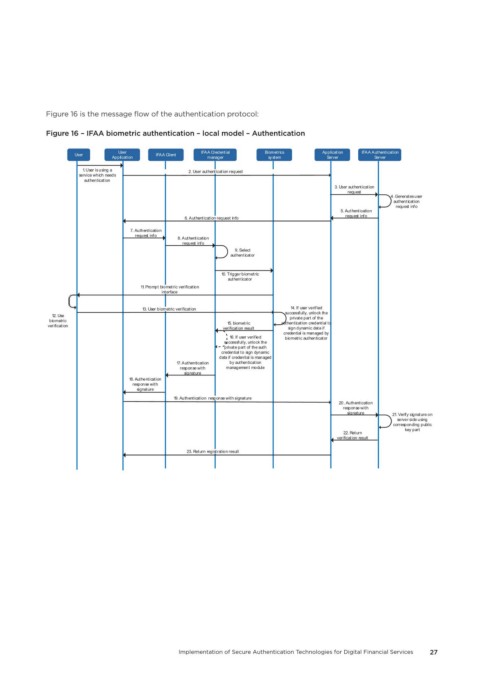
Figure 16 is the message flow of the authentication protocol:
Figure 16 – IFAA biometric authentication – local model – Authentication
User IFAA Credential Biometrics Application IFAA Authentication
User IFAA Client
Application manager system Server Server
1. User is using a 2. User authentication request
service which needs
authentication
3. User authentication
request
4. Generates user
authentication
request info
5. Authentication
request info
6. Authentication request info
7. Authentication
request info
8. Authentication
request info
9. Select
authenticator
10. Trigger biometric
authenticator
11. Prompt biometric verification
interface
13. User biometric verification 14. If user verified
successfully, unlock the
12. Use
biometric private part of the
verification 15. biometric authentication credential to
verification result sign dynamic data if
credential is managed by
16. If user verified biometric authenticator
successfully, unlock the
private part of the auth
credential to sign dynamic
data if credential is managed
17. Authentication by authentication
response with management module
signature
18. Authentication
response with
signature
19. Authentication response with signature
20. Authentication
response with
signature 21. Verify signature on
server side using
corresponding public
key part
22. Return
verification result
23. Return registration result
Implementation of Secure Authentication Technologies for Digital Financial Services 27