Page 23 - Detecting deepfakes and generative AI: Report on standards for AI watermarking and multimedia authenticity workshop
P. 23
Detecting deepfakes and generative AI: Report on standards for AI
watermarking and multimedia authenticity workshop
of this technique is that it does not require the embedding of any information in the media
itself. It is immune to information removal because there is no information to remove.
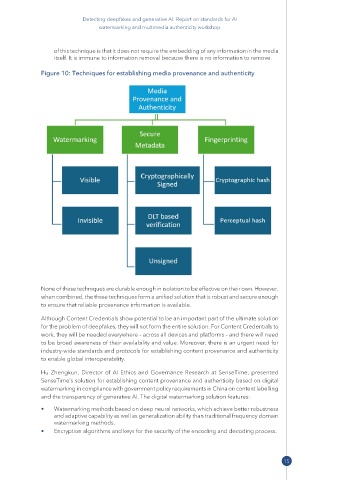
Figure 10: Techniques for establishing media provenance and authenticity
None of these techniques are durable enough in isolation to be effective on their own. However,
when combined, the three techniques form a unified solution that is robust and secure enough
to ensure that reliable provenance information is available.
Although Content Credentials show potential to be an important part of the ultimate solution
for the problem of deepfakes, they will not form the entire solution. For Content Credentials to
work, they will be needed everywhere – across all devices and platforms – and there will need
to be broad awareness of their availability and value. Moreover, there is an urgent need for
industry-wide standards and protocols for establishing content provenance and authenticity
to enable global interoperability.
Hu Zhengkun, Director of AI Ethics and Governance Research at SenseTime, presented
SenseTime’s solution for establishing content provenance and authenticity based on digital
watermarking in compliance with government policy requirements in China on content labelling
and the transparency of generative AI. The digital watermarking solution features:
• Watermarking methods based on deep neural networks, which achieve better robustness
and adaptive capability as well as generalization ability than traditional frequency domain
watermarking methods.
• Encryption algorithms and keys for the security of the encoding and decoding process.
15