Page 386 - Kaleidoscope Academic Conference Proceedings 2024
P. 386
2024 ITU Kaleidoscope Academic Conference
privacy queries can be performed without leaving the 5.2 End-to-end Transmission Security
original data.
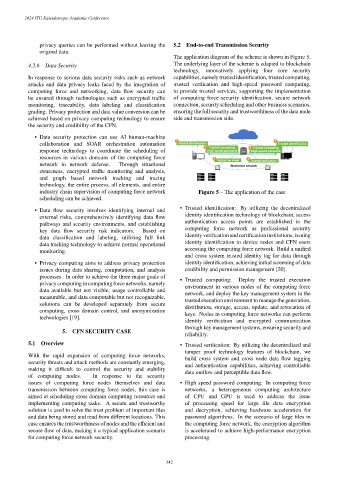
The application diagram of the scheme is shown in Figure 5.
4.2.6 Data Security The underlying layer of the scheme is adapted to blockchain
technology, innovatively applying four core security
In response to serious data security risks such as network capabilities, namely trusted identification, trusted computing,
attacks and data privacy leaks faced by the integration of trusted verification and high-speed password computing,
computing force and networking, data flow security can to provide trusted services, supporting the implementation
be ensured through technologies such as encrypted traffic of computing force security identification, secure network
monitoring, traceability, data labeling and classification connection, security scheduling and other business scenarios,
grading. Privacy protection and data value conversion can be ensuring the full security and trustworthiness of the data node
achieved based on privacy computing technology to ensure side and transmission side.
the security and credibility of the CFN.
• Data security protection can use AI human-machine
collaboration and SOAR orchestration automation
response technology to coordinate the scheduling of
resources in various domains of the computing force
network in network defense. Through situational
awareness, encrypted traffic monitoring and analysis,
and graph based network tracking and tracing
technology, the entire process, all elements, and entire
industry chain supervision of computing force network Figure 5 – The application of the case
scheduling can be achieved.
• Trusted identification: By utilizing the decentralized
• Data flow security involves identifying internal and
identity identification technology of blockchain, access
external risks, comprehensively identifying data flow
authentication access points are established in the
pathways and security environments, and establishing
computing force network as professional security
key data flow security risk indicators. Based on
identity verification and certification institutions, issuing
data classification and labeling, utilizing full link
identity identification to device nodes and CFN users
data tracking technology to achieve normal operational
accessing the computing force network. Build a unified
monitoring.
and cross system trusted identity tag for data through
• Privacy computing aims to address privacy protection identity identification, achieving initial screening of data
issues during data sharing, computation, and analysis credibility and permission management [20].
processes. In order to achieve the three major goals of
• Trusted computing: Deploy the trusted execution
privacy computing in computing force networks, namely
environment in various nodes of the computing force
data available but not visible, usage controllable and
network, and deploy the key management system in the
measurable, and data computable but not recognizable,
trusted execution environment to manage the generation,
solutions can be developed separately from secure
distribution, storage, access, update, and revocation of
computing, cross domain control, and anonymization
keys. Nodes in computing force networks can perform
technologies [19].
identity verification and encrypted communication
through key management systems, ensuring security and
5. CFN SECURITY CASE
reliability.
5.1 Overview • Trusted verification: By utilizing the decentralized and
tamper proof technology features of blockchain, we
With the rapid expansion of computing force networks,
build cross system and cross node data flow tagging
security threats and attack methods are constantly emerging,
and authentication capabilities, achieving controllable
making it difficult to control the security and stability
data outflow and perceptible data flow.
of computing nodes. In response to the security
issues of computing force nodes themselves and data • High speed password computing: In computing force
transmission between computing force nodes, this case is networks, a heterogeneous computing architecture
aimed at scheduling cross domain computing resources and of CPU and GPU is used to address the issue
implementing computing tasks. A secure and trustworthy of processing speed for large file data encryption
solution is used to solve the trust problem of important files and decryption, achieving hardware acceleration for
and data being stored and read from different locations. This password algorithms. In the scenario of large files in
case ensures the trustworthiness of nodes and the efficient and the computing force network, the encryption algorithm
secure flow of data, making it a typical application scenario is accelerated to achieve high-performance encryption
for computing force network security. processing.
– 342 –