Page 381 - Kaleidoscope Academic Conference Proceedings 2024
P. 381
COMPUTING FORCE NETWORK SECURITY: RISKS, PROTECTION REQUIREMENTS
AND SCENARIOS
Hongju, Sun; Qin, Qiu; Jiawei, Xu ; Tianni, Xu ; Sijia, Xu ; Feng, Zhang
China Mobile Communications Group Co., Ltd, China
ABSTRACT
Computing force infrastructure is a new type of information
infrastructure with computing as the center and network
as the foundation. The development trend of integrated
computing and networking has enriched and expanded the
supply, application, and service methods of computing force,
playing an important role in empowering and increasing
efficiency in the industry. However, it has also brought
new security challenges and increased the difficulty of
security protection. Based on the successful industry
practice, this paper puts forward the computing force network
(CFN) security protection requirements for operators and
industry customers. The goal of these policies is to help
industry customers achieve the three synchronization of
security (synchronous planning, synchronous construction,
and synchronous maintenance) when building CFN, and to
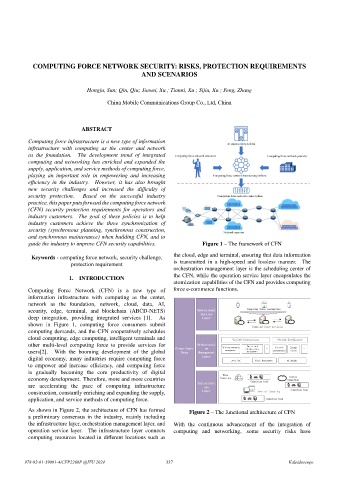
guide the industry to improve CFN security capabilities. Figure 1 – The framework of CFN
the cloud, edge and terminal, ensuring that data information
Keywords - computing force network, security challenge,
is transmitted in a high-speed and lossless manner. The
protection requirement
orchestration management layer is the scheduling center of
the CFN, while the operation service layer encapsulates the
1. INTRODUCTION
atomization capabilities of the CFN and provides computing
Computing Force Network (CFN) is a new type of force e-commerce functions.
information infrastructure with computing as the center,
network as the foundation, network, cloud, data, AI,
security, edge, terminal, and blockchain (ABCD-NETS)
deep integration, providing integrated services [1]. As
shown in Figure 1, computing force consumers submit
computing demands, and the CFN cooperatively schedules
cloud computing, edge computing, intelligent terminals and
other multi-level computing force to provide services for
users[2]. With the booming development of the global
digital economy, many industries require computing force
to empower and increase efficiency, and computing force
is gradually becoming the core productivity of digital
economy development. Therefore, more and more countries
are accelerating the pace of computing infrastructure
construction, constantly enriching and expanding the supply,
application, and service methods of computing force.
As shown in Figure 2, the architecture of CFN has formed
Figure 2 – The functional architecture of CFN
a preliminary consensus in the industry, mainly including
the infrastructure layer, orchestration management layer, and With the continuous advancement of the integration of
operation service layer. The infrastructure layer connects computing and networking, some security risks have
computing resources located in different locations such as
978-92-61-39091-4/CFP2268P @ITU 2024 – 337 – Kaleidoscope