Page 384 - Kaleidoscope Academic Conference Proceedings 2024
P. 384
2024 ITU Kaleidoscope Academic Conference
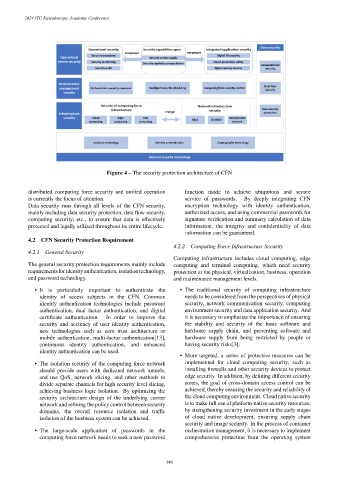
Figure 4 – The security protection architecture of CFN
distributed computing force security and unified operation function mode to achieve ubiquitous and secure
is currently the focus of attention. service of passwords. By deeply integrating CFN
Data security runs through all levels of the CFN security, encryption technology with identity authentication,
mainly including data security protection, data flow security, authorized access, and using commercial passwords for
computing security, etc., to ensure that data is effectively signature verification and summary calculation of data
protected and legally utilized throughout its entire lifecycle. information, the integrity and confidentiality of data
information can be guaranteed.
4.2 CFN Security Protection Requirement
4.2.2 Computing Force Infrastructure Security
4.2.1 General Security
Computing infrastructure includes cloud computing, edge
The general security protection requirements mainly include computing and terminal computing, which need security
requirements for identity authentication, isolation technology, protection at the physical, virtualization, business, operation
and password technology. and maintenance management levels.
• It is particularly important to authenticate the • The traditional security of computing infrastructure
identity of access subjects in the CFN. Common needs to be considered from the perspectives of physical
identity authentication technologies include password security, network communication security, computing
authentication, dual factor authentication, and digital environment security and data application security. And
certificate authentication. In order to improve the it is necessary to emphasize the importance of ensuring
security and accuracy of user identity authentication, the stability and security of the basic software and
new technologies such as zero trust architecture or hardware supply chain, and preventing software and
mobile authentication, multi-factor authentication[13], hardware supply from being restricted by people or
continuous identity authentication, and enhanced having security risks[3].
identity authentication can be used.
• More targeted, a series of protective measures can be
• The isolation security of the computing force network implemented for cloud computing security, such as
should provide users with dedicated network tunnels, installing firewalls and other security devices to protect
and use QoS, network slicing, and other methods to edge security. In addition, by defining different security
divide separate channels for high security level slicing, zones, the goal of cross-domain access control can be
achieving business logic isolation. By optimizing the achieved, thereby ensuring the security and reliability of
security architecture design of the underlying carrier the cloud computing environment. Cloud native security
network and refining the policy control between security is to make full use of platform-native security resources,
domains, the overall resource isolation and traffic by strengthening security investment in the early stages
isolation of the business system can be achieved. of cloud native development, ensuring supply chain
security and image security. In the process of container
• The large-scale application of passwords in the orchestration management, it is necessary to implement
computing force network needs to seek a new password comprehensive protection from the operating system
– 340 –