Page 314 - Kaleidoscope Academic Conference Proceedings 2024
P. 314
2024 ITU Kaleidoscope Academic Conference
Employing blockchain technology for encoding and marking
data with trustworthy techniques, this approach generates
distributed data credentials based on blockchain, serving as
the basis for data verification, authentication, and tracking,
ensuring the security and trustworthiness of signed data.
Commercial cryptographic algorithm and hash algorithms
are used to ensure the authenticity, integrity, privacy, and
security of data on the blockchain. The structure of one block
and the chain is shown in Figure 4.
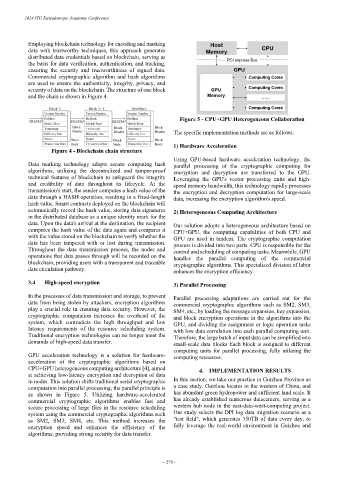
Figure 5 - CPU+GPU Heterogeneous Collaboration
The specific implementation methods are as follows:
1) Hardware Acceleration
Figure 4 - Blockchain chain structure
Using GPU-based hardware acceleration technology, the
Data marking technology adopts secure computing hash parallel processing of the cryptographic computing for
algorithms, utilizing the decentralized and tamper-proof encryption and decryption are transferred to the GPU.
technical features of blockchain to safeguard the integrity Leveraging the GPU's vector processing units and high-
and credibility of data throughout its lifecycle. At the speed memory bandwidth, this technology rapidly processes
transmission's start, the sender computes a hash value of the the encryption and decryption computation for large-scale
data through a HASH operation, resulting in a fixed-length data, increasing the encryption algorithm's speed.
hash value. Smart contracts deployed on the blockchain will
automatically record the hash value, storing data signatures 2) Heterogeneous Computing Architecture
in the distributed database as a unique identity mark for the
data. Upon the data's arrival at the destination, the recipient Our solution adopts a heterogeneous architecture based on
computes the hash value of the data again and compares it CPU+GPU, the computing capabilities of both CPU and
with the value stored on the blockchain to verify whether the GPU are used in tandem. The cryptographic computation
data has been tampered with or lost during transmission. process is divided into two parts. CPU is responsible for the
Throughout the data transmission process, the nodes and control and scheduling of computing tasks. Meanwhile, GPU
operations that data passes through will be recorded on the handles the parallel computing of the commercial
blockchain, providing users with a transparent and traceable cryptographic algorithms. This specialized division of labor
data circulation pathway. enhances the encryption efficiency.
3.4 High-speed encryption 3) Parallel Processing
In the processes of data transmission and storage, to prevent Parallel processing adaptations are carried out for the
data from being stolen by attackers, encryption algorithms commercial cryptographic algorithms such as SM2, SM3,
play a crucial role in ensuring data security. However, the SM4, etc., by loading the message expansion, key expansion,
cryptographic computation increases the overhead of the and block encryption operations in the algorithms into the
system, which contradicts the high throughput and low GPU, and dividing the assignment or logic operation tasks
latency requirements of the resource scheduling system. with low data correlation into each parallel computing unit.
Traditional encryption technologies can no longer meet the Therefore, the large batch of input data can be simplified into
demands of high-speed data transfer. small-scale data blocks Each block is assigned to different
computing units for parallel processing, fully utilizing the
GPU acceleration technology is a solution for hardware- computing resources.
acceleration of the cryptographic algorithms based on
CPU+GPU heterogeneous computing architecture [4], aimed 4. IMPLEMENTATION RESULTS
at achieving low-latency encryption and decryption of data
in nodes. This solution shifts traditional serial cryptographic In this section, we take our practice in Guizhou Province as
computation into parallel processing, the parallel principle is a case study. Guizhou locates in the western of China, and
as shown in Figure 5. Utilizing hardware-accelerated has abundant green hydropower and sufficient land scale. It
commercial cryptographic algorithms enables fast and has already established numerous datacenters, serving as a
secure processing of large files in the resource scheduling western hub node in the east-data-west-computing project.
system using the commercial cryptographic algorithms such Our study selects the DPI log data migration scenario as a
as SM2, SM3, SM4, etc. This method increases the "test field", which generates 350TB of data every day, to
encryption speed and enhances the efficiency of the fully leverage the real-world environment in Guizhou and
algorithms, providing strong security for data transfer.
– 270 –