Page 815 - Cloud computing: From paradigm to operation
P. 815
Intercloud and interoperability 5
Title Access security in trusted inter-cloud
Figure (optional)
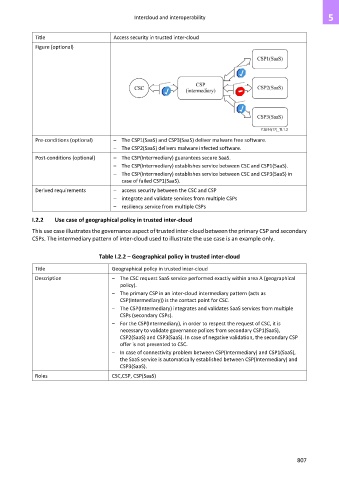
Pre-conditions (optional) – The CSP1(SaaS) and CSP3(SaaS) deliver malware free software.
– The CSP2(SaaS) delivers malware infected software.
Post-conditions (optional) – The CSP(Intermediary) guarantees secure SaaS.
– The CSP(Intermediary) establishes service between CSC and CSP1(SaaS).
– The CSP(Intermediary) establishes service between CSC and CSP3(SaaS) in
case of failed CSP1(SaaS).
Derived requirements – access security between the CSC and CSP
– integrate and validate services from multiple CSPs
– resiliency service from multiple CSPs
I.2.2 Use case of geographical policy in trusted inter-cloud
This use case illustrates the governance aspect of trusted inter-cloud between the primary CSP and secondary
CSPs. The intermediary pattern of inter-cloud used to illustrate the use case is an example only.
Table I.2.2 – Geographical policy in trusted inter-cloud
Title Geographical policy in trusted inter-cloud
Description – The CSC request SaaS service performed exactly within area A (geographical
policy).
– The primary CSP in an inter-cloud intermediary pattern (acts as
CSP(Intermediary)) is the contact point for CSC.
– The CSP(Intermediary) integrates and validates SaaS services from multiple
CSPs (secondary CSPs).
– For the CSP(Intermediary), in order to respect the request of CSC, it is
necessary to validate governance polices from secondary CSP1(SaaS),
CSP2(SaaS) and CSP3(SaaS). In case of negative validation, the secondary CSP
offer is not presented to CSC.
– In case of connectivity problem between CSP(Intermediary) and CSP1(SaaS),
the SaaS service is automatically established between CSP(Intermediary) and
CSP3(SaaS).
Roles CSC,CSP, CSP(SaaS)
807