Page 817 - Cloud computing: From paradigm to operation
P. 817
Intercloud and interoperability 5
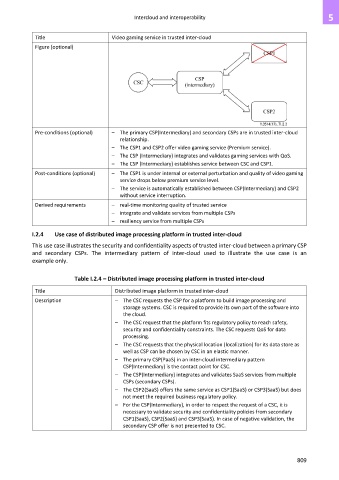
Title Video gaming service in trusted inter-cloud
Figure (optional)
Pre-conditions (optional) – The primary CSP(Intermediary) and secondary CSPs are in trusted inter-cloud
relationship.
– The CSP1 and CSP2 offer video gaming service (Premium service).
– The CSP (Intermediary) integrates and validates gaming services with QoS.
– The CSP (Intermediary) establishes service between CSC and CSP1.
Post-conditions (optional) – The CSP1 is under internal or external perturbation and quality of video gaming
service drops below premium service level.
– The service is automatically established between CSP(Intermediary) and CSP2
without service interruption.
Derived requirements – real-time monitoring quality of trusted service
– integrate and validate services from multiple CSPs
– resiliency service from multiple CSPs
I.2.4 Use case of distributed image processing platform in trusted inter-cloud
This use case illustrates the security and confidentiality aspects of trusted inter-cloud between a primary CSP
and secondary CSPs. The intermediary pattern of inter-cloud used to illustrate the use case is an
example only.
Table I.2.4 – Distributed image processing platform in trusted inter-cloud
Title Distributed image platform in trusted inter-cloud
Description – The CSC requests the CSP for a platform to build image processing and
storage systems. CSC is required to provide its own part of the software into
the cloud.
– The CSC request that the platform fits regulatory policy to reach safety,
security and confidentiality constraints. The CSC requests QoS for data
processing.
– The CSC requests that the physical location (localization) for its data store as
well as CSP can be chosen by CSC in an elastic manner.
– The primary CSP(PaaS) in an inter-cloud intermediary pattern
CSP(Intermediary) is the contact point for CSC.
– The CSP(Intermediary) integrates and validates SaaS services from multiple
CSPs (secondary CSPs).
– The CSP2(SaaS) offers the same service as CSP1(SaaS) or CSP3(SaaS) but does
not meet the required business regulatory policy.
– For the CSP(Intermediary), in order to respect the request of a CSC, it is
necessary to validate security and confidentiality policies from secondary
CSP1(SaaS), CSP2(SaaS) and CSP3(SaaS). In case of negative validation, the
secondary CSP offer is not presented to CSC.
809