Page 353 - Cloud computing: From paradigm to operation
P. 353
Framework and requirements for cloud computing 1
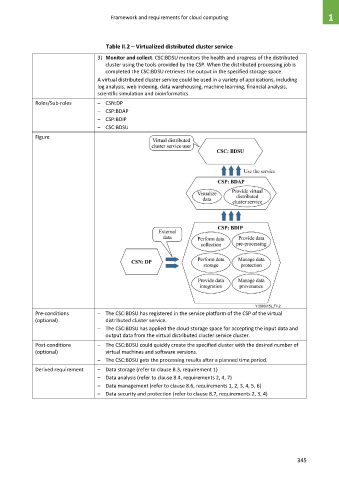
Table II.2 – Virtualized distributed cluster service
3) Monitor and collect. CSC:BDSU monitors the health and progress of the distributed
cluster using the tools provided by the CSP. When the distributed processing job is
completed the CSC:BDSU retrieves the output in the specified storage space.
A virtual distributed cluster service could be used in a variety of applications, including
log analysis, web indexing, data warehousing, machine learning, financial analysis,
scientific simulation and bioinformatics.
Roles/Sub-roles – CSN:DP
– CSP:BDAP
– CSP:BDIP
– CSC:BDSU
Figure
Pre-conditions – The CSC:BDSU has registered in the service platform of the CSP of the virtual
(optional) distributed cluster service.
– The CSC:BDSU has applied the cloud storage space for accepting the input data and
output data from the virtual distributed cluster service cluster.
Post-conditions – The CSC:BDSU could quickly create the specified cluster with the desired number of
(optional) virtual machines and software versions.
– The CSC:BDSU gets the processing results after a planned time period.
Derived requirement – Data storage (refer to clause 8.3, requirement 1)
– Data analysis (refer to clause 8.4, requirements 2, 4, 7)
– Data management (refer to clause 8.6, requirements 1, 2, 3, 4, 5, 6)
– Data security and protection (refer to clause 8.7, requirements 2, 3, 4)
345