Page 77 - Reference framework for integrated management of an SSC - A U4SSC deliverable on city platforms
P. 77
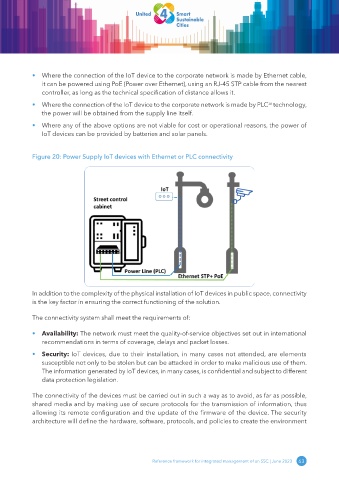
• Where the connection of the IoT device to the corporate network is made by Ethernet cable,
it can be powered using PoE (Power over Ethernet), using an RJ-45 STP cable from the nearest
controller, as long as the technical specification of distance allows it.
• Where the connection of the IoT device to the corporate network is made by PLC technology,
38
the power will be obtained from the supply line itself.
• Where any of the above options are not viable for cost or operational reasons, the power of
IoT devices can be provided by batteries and solar panels.
Figure 20: Power Supply IoT devices with Ethernet or PLC connectivity
In addition to the complexity of the physical installation of IoT devices in public space, connectivity
is the key factor in ensuring the correct functioning of the solution.
The connectivity system shall meet the requirements of:
• Availability: The network must meet the quality-of-service objectives set out in international
recommendations in terms of coverage, delays and packet losses.
• Security: IoT devices, due to their installation, in many cases not attended, are elements
susceptible not only to be stolen but can be attacked in order to make malicious use of them.
The information generated by IoT devices, in many cases, is confidential and subject to different
data protection legislation.
The connectivity of the devices must be carried out in such a way as to avoid, as far as possible,
shared media and by making use of secure protocols for the transmission of information, thus
allowing its remote configuration and the update of the firmware of the device. The security
architecture will define the hardware, software, protocols, and policies to create the environment
Reference framework for integrated management of an SSC | June 2023 63