Page 138 - Kaleidoscope Academic Conference Proceedings 2021
P. 138
2021 ITU Kaleidoscope Academic Conference
2. IOT-DOMOTICS REFERENCE MODEL Service subsystems mainly contains the operation &
management subsystem, application & service subsystem,
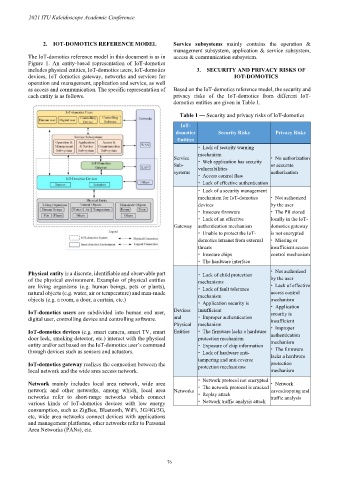
The IoT-domotics reference model in this document is as in access & communication subsystem.
Figure 1. An entity-based representation of IoT-domotics
includes physical entities, IoT-domotics users, IoT-domotics 3. SECURITY AND PRIVACY RISKS OF
devices, IoT domotics gateway, networks and services for IOT-DOMOTICS
operation and management, application and service, as well
as access and communication. The specific representation of Based on the IoT-domotics reference model, the security and
each entity is as follows. privacy risks of the IoT-domotics from different IoT-
domotics entities are given in Table 1.
Table 1 — Security and privacy risks of IoT-domotics
IoT-
domotics Security Risks Privacy Risks
Entities
Lack of security warning
mechanism
Service Web application has security No authorization
Sub- vulnerabilities or accurate
systems authorization
Access control flaw
Lack of effective authentication
Lack of a security management
mechanism for IoT-domotics Not authorized
devices by the user
Insecure firmware The PII stored
Lack of an effective locally in the IoT-
Gateway authentication mechanism domotics gateway
Unable to protect the IoT- is not encrypted
domotics intranet from external Missing or
threats insufficient access
Insecure chips control mechanism
The hardware interface
Physical entity is a discrete, identifiable and observable part Lack of child protection Not authorized
of the physical environment. Examples of physical entities mechanisms by the user
are living organisms (e.g. human beings, pets or plants), Lack of fault tolerance Lack of effective
natural objects (e.g. water, air or temperature) and man-made mechanism access control
objects (e.g. a room, a door, a curtain, etc.) mechanism
Application security is Application
IoT-domotics users are subdivided into human end user, Devices insufficient security is
digital user, controlling device and controlling software. and Improper authentication insufficient
Physical mechanism Improper
IoT-domotics devices (e.g. smart camera, smart TV, smart Entities The firmware lacks a hardware authentication
door lock, smoking detector, etc.) interact with the physical protection mechanism
entity and/or act based on the IoT-domotics user’s command Exposure of chip information mechanism
through devices such as sensors and actuators. Lack of hardware anti- The firmware
tampering and anti-reverse lacks a hardware
IoT-domotics gateway realizes the connection between the protection mechanisms protection
local network and the wide area access network. mechanism
Network protocol not encrypted
Network mainly includes local area network, wide area The network protocol is cracked Network
network and other networks, among which, local area Networks eavesdropping and
networks refer to short-range networks which connect Replay attack traffic analysis
various kinds of IoT-domotics devices with low energy Network traffic analysis attack
consumption, such as ZigBee, Bluetooth, WiFi, 3G/4G/5G,
etc, wide area networks connect devices with applications
and management platforms, other networks refer to Personal
Area Networks (PANs), etc.
– 76 –