Page 143 - Kaleidoscope Academic Conference Proceedings 2021
P. 143
Connecting physical and virtual worlds
Enhanced WiFi management function. The WiFi and opt out functions. The collection, storage, transmission
management function mechanism should be designed and and use of sensitive information must be authorized by IoT-
implemented. For unfamiliar devices that are connected to domotics users.
the IoT-domotics gateway for the first time, the IoT-
domotics gateway manager will determine whether to allow Privacy protection of applications. The privacy driver
the access of unfamiliar devices, and provide the IoT- should be embedded in the firmware. At the same time, the
domotics gateway manager with information that can easily application should adopt the principle of minimization when
view the access of IoT-domotics devices and manage the collecting personal information. Before storing or using PII,
access of IoT-domotics devices. it is necessary to de-identify or desensitize the data.
Provide privacy management tools. Security management Privacy security of device connection. Privacy security of
tools are equipped for privacy protection and management to domotics device connection should be designed and
prevent new privacy from being illegally collected and used. implemented. Use mature network privacy security
Flexible management and control of devices connected to the technology to reduce the risk of privacy security. High
gateway. Users can use common gateway management tools security network chips and modules are used to minimize the
to detect gateway vulnerabilities and upgrade firmware, as impact of technical vulnerabilities on IoT-domotics users.
well as other security management services.
Enhance the privacy protection of hardware. Provides
Provide hardware privacy protection. The hardware hardware control privacy options to prevent any background
control mechanism of privacy security should be designed program access. Provide device operation status indication
and implemented, for example, using security chips with options. Provide camera hiding function when the device
TEE or SE modules. Chip design, privacy protection circuit stops running.
and other security measures.
4.3.4 Privacy controls for networks
4.3.3 Privacy controls for IoT-domotics devices and
physical entities Privacy security of transmission in network. The same as
privacy controls of security controls for networks.
Transparency of PII in data life cycle. Inform IoT-
domotics users of the privacy policy in an easy to understand 5. SUPPORTING CONTROL SCHEMES
way, and provide IoT-domotics users with effective consent
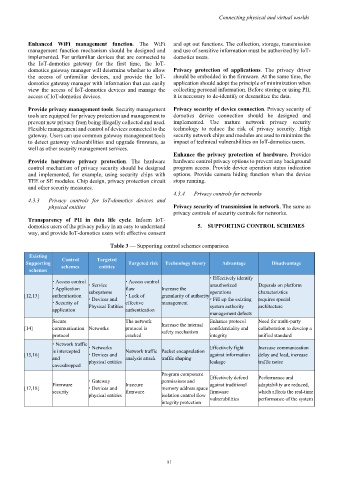
Table 3 — Supporting control schemes comparison
Existing Control Targeted
Supporting schemes entities Targeted risk Technology theory Advantage Disadvantage
schemes
Effectively identify
Access control Service Access control unauthorized Depends on platform
Application subsystems flaw Increase the operations characteristics
[12,13] authentication Devices and Lack of granularity of authority Fill up the existing requires special
Security of Physical Entities effective management system authority architecture
application authentication
management defects
Secure The network Enhance protocol Need for multi-party
[14] communication Networks protocol is Increase the internal confidentiality and collaboration to develop a
safety mechanism
protocol cracked integrity unified standard
Network traffic
is intercepted Networks Network traffic Packet encapsulation Effectively fight Increase communication
[15,16] Devices and against information delay and load, increase
and analysis attack traffic shaping
eavesdropped physical entities leakage traffic noise
Program component
Gateway permissions and Effectively defend Performance and
Firmware Insecure against traditional adaptability are reduced,
[17,18] Devices and memory address space
security firmware firmware which affects the real-time
physical entities isolation control flow vulnerabilities performance of the system
integrity protection
– 81 –