Page 112 - ITU Journal Future and evolving technologies Volume 2 (2021), Issue 1
P. 112
ITU Journal on Future and Evolving Technologies, Volume 2 (2021), Issue 1
dently of the RAT and based only on the routes’ costs and
performances. In this case and considering Table 6, the
best route for RV monitoring is the one toward the Sigfox base
station because low energy consumption is favored. The
best route for RV alarm is the one toward the NB‐IoT base
station because high bit rate is favored. then starts to
advertise and use its best routes.
8.2 Packet structure
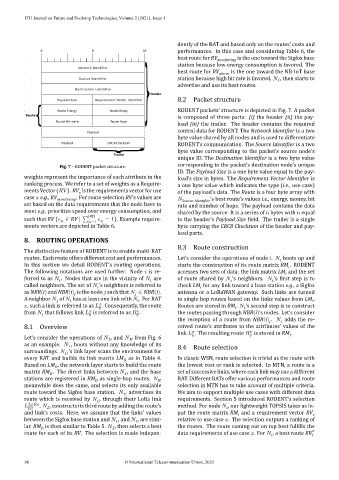
RODENT packets’ structure is depicted in Fig. 7. A packet
is composed of three parts: (i) the header (ii) the pay‐
load (iii) the trailer. The header contains the required
control data for RODENT. The Network Identifier is a two
byte value shared by all nodes and is used to differentiate
RODENT’s communication. The Source Identifier is a two
byte value corresponding to the packet’s source node’s
unique ID. The Destination Identifier is a two byte value
Fig. 7 – RODENT packet structure. corresponding to the packet’s destination node’s unique
ID. The Payload Size is a one byte value equal to the pay‐
weights represent the importance of each attribute in the load’s size in bytes. The Requirement Vector Identifier is
ranking process. We refer to a set of weights as a Require‐ a one byte value which indicates the type (i.e., use case)
mentsVector( ). RV istherequirementsvectorforuse of the payload’s data. The Route is a four byte array with
x
case e.g., RV monitoring . For route selection RV’s values are Source Identifier ’s best route’s values i.e., energy, money, bit
set based on the data requirements that the node have to rate and number of hops. The payload contains the data
meet e.g., prioritize speed over energy consumption, and shared by the source. It is a series of bytes with equal
such that RV { ∈ RV | ∑ |RV| = 1}. Example require‐ to the header’s Payload Size ield. The trailer is a single
=1
ments vectors are depicted in Table 6. byte carrying the CRC8 Checksum of the header and pay‐
load parts.
8. ROUTING OPERATIONS
8.3 Route construction
The distinctive feature of RODENT is to enable multi‐RAT
routes. Each route offers different cost and performances. Let’s consider the operations of node . boots up and
In this section we detail RODENT’s routing operations. starts the construction of its route matrix RM . RODENT
i
The following notations are used further. Node is re‐ accesses two sets of data: the link matrix LM and the set
i
ferred to as . Nodes that are in the vicinity of are of route shared by ’s neighbors. ’s irst step is to
called neighbors. The set of ’s neighbors is referred to check LM for any link toward a base station e.g., a Sigfox
i
as NBR(i) and NBR(i) is the node such that ∈ NBR(i). antenna or a LoRaWAN gateway. Such links are turned
j
A neighbor of has at least one link with . For RAT to single hop routes based on the links values from LM .
i
, such a link is referred to as . Consequently, the route Routes are stored in RM . ’s second step is to construct
i
ij
from that follows link is referred to as . the routes passing through NBR(i)’s nodes. Let’s consider
ij
ij
the reception of a route from NBR(i) . adds the re‐
j
8.1 Overview ceived route’s attributes to the attributes’ values of the
link . The resulting route is stored in RM .
Let’s consider the operations of and from Fig. 6 ij ij i
as an example. boots without any knowledge of its 8.4 Route selection
surroundings. ’s link layer scans the environment for
every RAT and builds its link matrix LM as in Table 4. In classic WSN, route selection is trivial as the route with
D
Based on LM , the network layer starts to build the route the lowest cost or rank is selected. In MTN, a route is a
D
matrix RM . The direct links between and the base set of successive links, where each link may use a different
D
stations are registered in RM as single‐hop routes. RAT. Different RATs offer various performances and route
D
meanwhile does the same, and selects its only available selection in MTN has to take account of multiple criteria.
route toward the Sigfox base station. advertises its We aim to support multiple use cases with different data
route which is received by through their LoRa link requirements. Section 5 introduced RODENT’s selection
. constructs its third route by adding the route’s method. For node , our lightweight TOPSIS takes as in‐
ED
and link’s costs. Here, we assume that the links’ values put the route matrix RM and a requirement vector RV x
i
between the Sigfox base station and and are simi‐ relative to use case . The selection outputs a ranking of
lar. RM is then similar to Table 5. then selects a best the routes. The route coming out on top best ful ills the
D
route for each of its RV. The selection is made indepen‐ data requirements of use case . For , a best route BR
96 © International Telecommunication Union, 2021