Page 18 - FIGI: Digital Financial Services security audit guideline
P. 18
(continued)
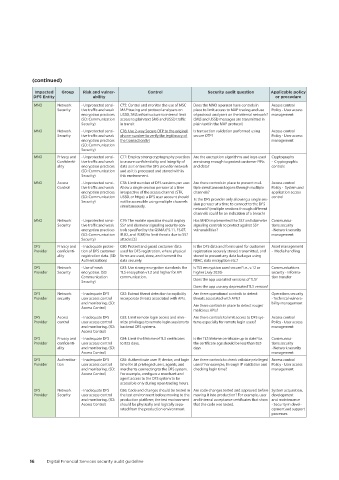
Impacted Group Risk and vulner- Control Security audit question Applicable policy
DFS Entity ability or procedure
MNO Network - Unprotected sensi- C75: Control and monitor the use of MSC Does the MNO operator have controls in Access control
Security tive traffic and weak MAP tracing and protocol analysers on place to limit access to MAP tracing and use Policy - User access
encryption practices USSD, SMS infrastructure to internal limit of protocol analysers on the internal network? management
(SD: Communication access to plain text SMS and USSD traffic (SMS and USSD messages are transmitted in
Security) in transit plain text in the MAP protocol)
MNO Network - Unprotected sensi- C76: Use 2-way Secure OTP to the original Is transaction validation performed using Access control
Security tive traffic and weak phone number to verify the legitimacy of secure OTP? Policy - User access
encryption practices the transaction[iv] management
(SD: Communication
Security)
MNO Privacy and - Unprotected sensi- C77: Employ strong cryptography practices Are the encryption algorithms and keys used Cryptography
Confidenti- tive traffic and weak to assure confidentiality and integrity of are strong enough to protect customer PINs - Cryptographic
ality encryption practices data as it enters the DFS provider network and data? controls
(SD: Communication and as it is processed and stored within
Security) this environment.
MNO Access - Unprotected sensi- C78: Limit number of DFS sessions per user. Are there controls in place to prevent mul- Access control
Control tive traffic and weak Allow a single session per user at a time tiple simultaneous logons through multiple Policy - System and
encryption practices irrespective of the access channel (STK, channels? application access
(SD: Communication USSD, or https); a DFS user account should control
Security) not be accessible using multiple channels Is the DFS provider only allowing a single ses-
sion per user at a time to connect to the DFS
simultaneously.
network? (multiple sessions through different
channels could be an indication of a breach)
MNO Network - Unprotected sensi- C79: The mobile operator should deploy Has MNO implemented the SS7 and diameter Communica-
Security tive traffic and weak SS7 and diameter signaling security con- signaling controls to protect against SS7 tions security
encryption practices trols specified by the GSMA (FS.11, FS.07, vulnerabilities? - Network security
(SD: Communication IR.82, and IR.88) to limit threats due to SS7 management
Security) attacks [3]
DFS Privacy and - Inadequate protec- C80: Protect and guard customer data Is the DFS data and forms used for customer Asset management
Provider confidenti- tion of DFS customer used for DFS registration, where physical registration securely stored, transmitted, and - Media handling
ality registration data. (SD: forms are used, store, and transmit the stored to prevent any data leakages using
Authentication) data securely. RBAC, data encryption etc.?
DFS Network - Use of weak C81: Use strong encryption standards like Is TLS encryption used secure? i.e., v.12 or Communications
Provider Security encryption. (SD: TLS encryption v1.2 and higher for API higher (July 2020) security - Informa-
Communication communication. Does the app use latest versions of TLS? tion transfer
Security)
Does the app use any deprecated TLS version?
DFS Network - Inadequate DFS C82: Extend threat detection to explicitly Are there operational controls to detect Operations security
Provider security user access control incorporate threats associated with APIs. threats associated with APIs? - Technical vulnera-
and monitoring. (SD: Are there controls in place to detect rouge/ bility management
Access Control)
malicious APIs?
DFS Access - Inadequate DFS C83: Limit remote login access and mini- Are there controls to limit access to DFS sys- Access control
Provider control user access control mize privileges to remote login sessions to tems especially for remote login users? Policy - User access
and monitoring. (SD: backend DFS systems. management
Access Control)
DFS Privacy and - Inadequate DFS C84: Limit the lifetime of TLS certificates Is the TLS lifetime certificate up to date? I.e. Communica-
Provider confidenti- user access control to 825 days. the certificate age should be less than 825 tions security
ality and monitoring. (SD: days - Network security
Access Control) management
DFS Authentica- - Inadequate DFS C85: Authenticate user IP, device, and login Are there controls to check validate privileged Access control
Provider tion user access control time for all privileged users, agents, and users? For example, through IP validation and Policy - User access
and monitoring. (SD: merchants connecting to the DFS system. checking login time? management
Access Control) For example, configure a merchant and
agent access to the DFS system to be
accessible only during open trading hours.
DFS Network - Inadequate DFS C86: Code and changes should be tested in Are code changes tested and approved before System acquisition,
Provider Security user access control the test environment before moving to the moving it into production? For example, user development
and monitoring. (SD: production platform; the test environment and internal acceptance certificates that show and maintenance
Access Control) should be physically and logically sepa- that the code was tested. - Security in devel-
rated from the production environment. opment and support
processes
16 Digital Financial Services security audit guideline