Page 11 - FIGI: Digital Financial Services security audit guideline
P. 11
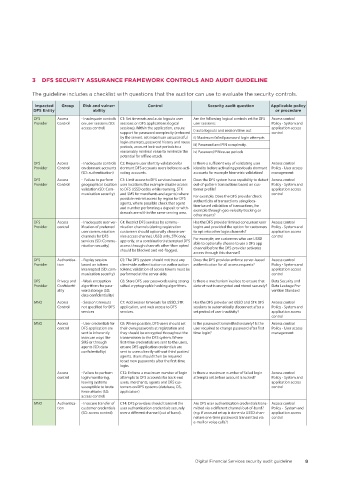
3 DFS SECURITY ASSURANCE FRAMEWORK CONTROLS AND AUDIT GUIDELINE
The guideline includes a checklist with questions that the auditor can use to evaluate the security controls.
Impacted Group Risk and vulner- Control Security audit question Applicable policy
DFS Entity ability or procedure
DFS Access - Inadequate controls C1: Set timeouts and auto logouts user Are the following logical controls set for DFS Access control
Provider Control on user sessions (SD: sessions on DFS applications (logical user sessions: Policy - System and
access control) sessions). Within the application, ensure i) auto logouts and session time out application access
support for password complexity (enforced control
by the server), set maximum unsuccessful ii) Maximum failed password login attempts
login attempts, password history and reuse
periods, account lock-out periods to a iii) Password and PIN complexity.
reasonably minimal value to minimize the iv) Password/PIN reuse periods
potential for offline attack
DFS Access - Inadequate controls C2: Require user identity validation for Is there a sufficient way of validating user Access control
Provider Control on dormant accounts dormant DFS accounts users before re-acti- identity before activating previously dormant Policy - User access
(SD: authentication) vating accounts. accounts for example biometric validation? management
DFS Access - Failure to perform C3: Limit access to DFS services based on Does the DFS system have capability to detect Access control
Provider Control geographical location user locations (for example disable access out-of-pattern transactions based on cus- Policy - System and
validation (SD: Com- to DFS USSD codes while roaming, STK tomer profile? application access
munication security) and SMS for merchants and agents) where For example: Does the DFS provider check control
possible restrict access by region for DFS
agents, where possible check that agent authenticity of transactions using loca-
tion-based validation of transactions, for
and number performing a deposit or with- example through geo-velocity tracking or
drawals are within the same serving area.
other means?
DFS Access - Inadequate user ver- C4: Restrict DFS services by commu- Has the DFS provider limited concurrent user Access control
Provider control ification of preferred nication channels (during registration logins and provided the option for customers Policy - System and
user communication customers should optionally choose ser- to opt into other login channels? application access
channels for DFS vice access channel, USSD only, STK only, control
services (SD: Commu- app only, or a combination) attempted DFS For example, are customers who use USSD
able to optionally choose to use a DFS app
nication security) access through channels other than opted channel before the DFS provider activates
should be blocked and red-flagged.
access through this channel?
DFS Authentica- - Replay session C5: The DFS system should not trust any Does the DFS provider enforce server-based Access control
Provider tion based on tokens client-side authentication or authorization authentication for all access requests? Policy - System and
intercepted (SD: com- tokens; validation of access tokens must be application access
munication security) performed at the server-side. control
DFS Privacy and - Weak encryption C6: Store DFS user passwords using strong Is there a mechanism in place to ensure that Data Security and
Provider Confidenti- algorithms for pass- salted cryptographic hashing algorithms. data-at-rest is encrypted and stored securely? Data Leakage Pre-
ality word storage (SD: vention Standard
data confidentiality)
MNO Access - Session timeouts C7: Add session timeouts for USSD, STK Has the DFS provider set USSD and STK DFS Access control
Control not specified for DFS application, and web access to DFS sessions to automatically disconnect after a Policy - System and
services services. set period of user inactivity? application access
control
MNO Access - User credentials for C8: Where possible, DFS users should set Is the password transmitted securely? Is the Access control
control DFS application are their own passwords at registration and user required to change password after first Policy - User access
sent in inherently they should be encrypted throughout the time login? management
insecure ways like transmission to the DFS system. Where
SMS or through first-time credentials are sent to the users,
agents (SD: data ensure DFS application credentials are
confidentiality) sent to users directly without third parties/
agents. Users should then be required
to set new passwords after the first-time
login.
Access - Failure to perform C12: Enforce a maximum number of login Is there a maximum number of failed login Access control
control login monitoring, attempts to DFS accounts for back-end attempts set before account is locked? Policy - System and
leaving systems users, merchants, agents and DFS cus- application access
susceptible to brute tomers on DFS systems (database, OS, control
force attacks (SD: application)
access control)
MNO Authentica- - Insecure transfer of C14: DFS providers should transmit the Are DFS user authentication credentials trans- Access control
tion customer credentials user authentication credentials securely mitted via a different channel/out-of-band? Policy - System and
(SD: access control) over a different channel (out of band). (e.g. if account setup is done via USSD chan- application access
nel are one-time passwords transmitted via control
e-mail or voice calls?)
Digital Financial Services security audit guideline 9