Page 33 - FIGI Digital Financial Services security assurance framework
P. 33
(continued)
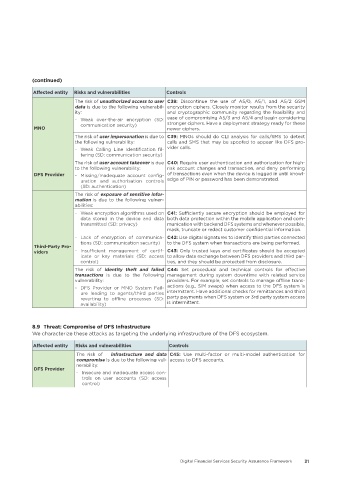
Affected entity Risks and vulnerabilities Controls
The risk of unauthorized access to user C38: Discontinue the use of A5/0, A5/1, and A5/2 GSM
data is due to the following vulnerabil- encryption ciphers. Closely monitor results from the security
ity: and cryptographic community regarding the feasibility and
- Weak over-the-air encryption (SD: ease of compromising A5/3 and A5/4 and begin considering
communication security) stronger ciphers. Have a deployment strategy ready for these
MNO newer ciphers.
The risk of user impersonation is due to C39: MNOs should do CLI analysis for calls/SMS to detect
the following vulnerability: calls and SMS that may be spoofed to appear like DFS pro-
- Weak Calling Line Identification fil- vider calls.
tering (SD: communication security)
The risk of user account takeover is due C40: Require user authentication and authorization for high-
to the following vulnerability: risk account changes and transaction, and deny performing
DFS Provider - Missing/Inadequate account config- of transactions even when the device is logged in until knowl-
uration and authorisation controls edge of PIN or password has been demonstrated.
(SD: authentication)
The risk of exposure of sensitive infor-
mation is due to the following vulner-
abilities:
- Weak encryption algorithms used on C41: Sufficiently secure encryption should be employed for
data stored in the device and data both data protection within the mobile application and com-
transmitted (SD: privacy) munication with backend DFS systems and whenever possible,
mask, truncate or redact customer confidential information.
- Lack of encryption of communica- C42: Use digital signatures to identify third parties connected
tions (SD: communication security) to the DFS system when transactions are being performed.
Third-Party Pro-
viders - Insufficient management of certif- C43: Only trusted keys and certificates should be accepted
icate or key materials (SD: access to allow data exchange between DFS providers and third par-
control) ties, and they should be protected from disclosure.
The risk of identity theft and failed C44: Set procedural and technical controls for effective
transactions is due to the following management during system downtime with related service
vulnerability: providers. For example, set controls to manage offline trans-
- DFS Provider or MNO System Fail- actions (e.g., SIM swaps) when access to the DFS system is
ure leading to agents/third parties intermittent. Have additional checks for remittances and third
reverting to offline processes (SD: party payments when DFS system or 3rd party system access
availability) is intermittent.
8�9 Threat: Compromise of DFS Infrastructure
We characterize these attacks as targeting the underlying infrastructure of the DFS ecosystem.
Affected entity Risks and vulnerabilities Controls
The risk of infrastructure and data C45: Use multi-factor or multi-model authentication for
compromise is due to the following vul- access to DFS accounts.
nerability:
DFS Provider
- Insecure and inadequate access con-
trols on user accounts (SD: access
control)
Digital Financial Services Security Assurance Framework 31