Page 29 - FIGI Digital Financial Services security assurance framework
P. 29
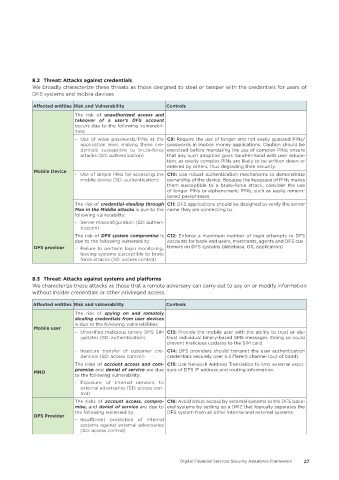
8�2 Threat: Attacks against credentials
We broadly characterize these threats as those designed to steal or tamper with the credentials for users of
DFS systems and mobile devices
Affected entities Risk and Vulnerability Controls
The risk of unauthorized access and
takeover of a user’s DFS account
occurs due to the following vulnerabil-
ities:
- Use of weak passwords/PINs at the C9: Require the use of longer and not easily guessed PINs/
application level, making these cre- passwords in mobile money applications. Caution should be
dentials susceptible to brute-force exercised before mandating the use of complex PINs; ensure
attacks (SD: authentication) that any such adoption goes hand-in-hand with user educa-
tion, as overly complex PINs are likely to be written down or
entered by others, thus degrading their security.
Mobile Device
- Use of simple PINs for accessing the C10: Use robust authentication mechanisms to demonstrate
mobile device (SD: authentication) ownership of the device. Because the keyspace of PINs makes
them susceptible to a brute-force attack, consider the use
of longer PINs or alphanumeric PINs, such as easily remem-
bered passphrases.
The risk of credential-stealing through C11: DFS applications should be designed to verify the server
Man in the Middle attacks is due to the name they are connecting to.
following vulnerability:
- Server misconfiguration (SD: authen-
tication)
The risk of DFS system compromise is C12: Enforce a maximum number of login attempts to DFS
due to the following vulnerability: accounts for back-end users, merchants, agents and DFS cus-
DFS provider - Failure to perform login monitoring, tomers on DFS systems (database, OS, application)
leaving systems susceptible to brute
force attacks (SD: access control)
8�3 Threat: Attacks against systems and platforms
We characterize these attacks as those that a remote adversary can carry out to spy on or modify information
without insider credentials or other privileged access.
Affected entities Risk and vulnerability Controls
The risk of spying on and remotely
stealing credentials from user devices
is due to the following vulnerabilities:
Mobile user
- Unverified malicious binary SMS SIM C13: Provide the mobile user with the ability to trust or dis-
updates (SD: authentication) trust individual binary-based SMS messages. Doing so could
prevent malicious updates to the SIM card
- Insecure transfer of customer cre- C14: DFS providers should transmit the user authentication
dentials (SD: access control) credentials securely over a different channel (out of band).
The risks of account access and com- C15: Use Network Address Translation to limit external expo-
MNO promise and denial of service are due sure of DFS IP address and routing information.
to the following vulnerability:
- Exposure of internal network to
external adversaries (SD: access con-
trol)
The risks of account access, compro- C16: Avoid direct access by external systems to the DFS back-
mise, and denial of service are due to end systems by setting up a DMZ that logically separates the
the following vulnerability: DFS system from all other internal and external systems.
DFS Provider
- Insufficient protection of internal
systems against external adversaries
(SD: access control)
Digital Financial Services Security Assurance Framework 27