Page 178 - Kaleidoscope Academic Conference Proceedings 2020
P. 178
2020 ITU Kaleidoscope Academic Conference
processing is under the CNN environment. Figure 5 shows
Data
Data the configuration of the CNN used to evaluate the proposed
Real data
suspicious object detection system. In addition to the input
Real
Discriminator or
Fake and output layers, it includes five main types of layers:
convolution, pooling, batch normalization, flatten, and fully
Z Data
(noise) Generator Data connected. The network parameters for each layer are given in
Fake data
Table 1. In this experiment, we used four types of suspicious
objects for the training and evaluation of the CNN: gun, knife,
Figure 3 – GAN architecture
scissor and others.
data and maps this noise so that it approaches the desired
data. The other is Discriminator, which gives the fake data 4.1 CASE 1
generated by the Generator and the real data, then judges the
authenticity. By competing these two networks alternately
and advancing learning, the Generator will be able to generate
fake data that is close to real data, and the Discriminator
sees it as a fake. Generator then evolves the technology
to create more sophisticated counterfeits. These “playing
games” are repeated, and eventually a counterfeit that is
close to the real thing will be generated. In this paper,
it is challenging to establish a complete suspicious object
database only by active/passive imagers’ experiments and
simulations. To address this issue, we generate a large number
of millimeter-wave images by GAN based on the original
images, which will be used for CNN training. Figure 4 shows
an example of GAN images which include gun, knife, other
and scissor.
Original images (experiments) Figure 6 – System architecture
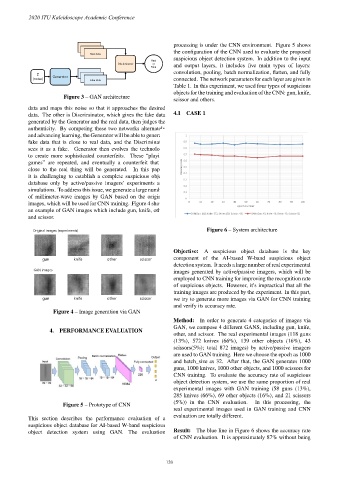
Objective: A suspicious object database is the key
gun knife other scissor component of the AI-based W-band suspicious object
detection system. It needs a large number of real experimental
GAN images
images generated by active/passive imagers, which will be
employed to CNN training for improving the recognition rate
of suspicious objects. However, it’s impractical that all the
training images are produced by the experiment. In this part,
gun knife other scissor we try to generate more images via GAN for CNN training
and verify its accuracy rate.
Figure 4 – Image generation via GAN
Method: In order to generate 4 categories of images via
GAN, we compose 4 different GANS, including gun, knife,
4. PERFORMANCE EVALUATION
other, and scissor. The real experimental images (118 guns
(13%), 572 knives (66%), 139 other objects (16%), 43
scissors(5%); total 872 images) by active/passive imagers
are used to GAN training. Here we choose the epoch as 1000
and batch_size as 32. After that, the GAN generates 1000
guns, 1000 knives, 1000 other objects, and 1000 scissors for
CNN training. To evaluate the accuracy rate of suspicious
object detection system, we use the same proportion of real
experimental images with GAN training (58 guns (13%),
285 knives (66%), 69 other objects (16%), and 21 scissors
(5%)) in the CNN evaluation. In this processing, the
Figure 5 – Prototype of CNN
real experimental images used in GAN training and CNN
evaluation are totally different.
This section describes the performance evaluation of a
suspicious object database for AI-based W-band suspicious
object detection system using GAN. The evaluation Result: The blue line in Figure 6 shows the accuracy rate
of CNN evaluation. It is approximately 87% without being
– 120 –