Page 52 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 52
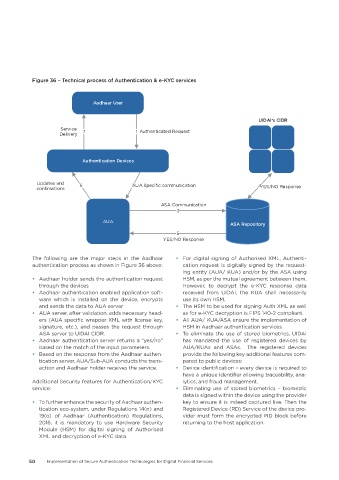
Figure 36 – Technical process of Authentication & e-KYC services
Aadhaar User
UIDAI s CIDR
Service 7 1 Authenticated Request
Delivery
Authentication Devices
Updates and AUA Specific communication
confimations YES/NO Response
ASA Communication
3
AUA
ASA Repository
5
YES/NO Response
The following are the major steps in the Aadhaar • For digital signing of Authorised XML, Authenti-
authentication process as shown in Figure 36 above: cation request is digitally signed by the request-
ing entity (AUA/ KUA) and/or by the ASA using
• Aadhaar holder sends the authentication request HSM, as per the mutual agreement between them.
through the devices However, to decrypt the e-KYC response data
• Aadhaar authentication enabled application soft- received from UIDAI, the KUA shall necessarily
ware which is installed on the device, encrypts use its own HSM.
and sends the data to AUA server • The HSM to be used for signing Auth XML as well
• AUA server, after validation, adds necessary head- as for e-KYC decryption is FIPS 140-2 compliant.
ers (AUA specific wrapper XML with license key, • All AUA/ KUA/ASA ensure the implementation of
signature, etc.), and passes the request through HSM in Aadhaar authentication services.
ASA server to UIDAI CIDR. • To eliminate the use of stored biometrics, UIDAI
• Aadhaar authentication server returns a “yes/no” has mandated the use of registered devices by
based on the match of the input parameters. AUA/KUAs and ASAs. The registered devices
• Based on the response from the Aadhaar authen- provide the following key additional features com-
tication server, AUA/Sub-AUA conducts the trans- pared to public devices:
action and Aadhaar holder receives the service. • Device identification – every device is required to
have a unique identifier allowing traceability, ana-
Additional Security features for Authentication/KYC lytics, and fraud management.
service: • Eliminating use of stored biometrics – biometric
data is signed within the device using the provider
• To further enhance the security of Aadhaar authen- key to ensure it is indeed captured live. Then the
tication eco-system, under Regulations 14(n) and Registered Device (RD) Service of the device pro-
19(o) of Aadhaar (Authentication) Regulations, vider must form the encrypted PID block before
2016, it is mandatory to use Hardware Security returning to the host application.
Module (HSM) for digital signing of Authorised
XML and decryption of e-KYC data.
50 Implementation of Secure Authentication Technologies for Digital Financial Services