Page 49 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 49
(continued)
⑥ Server Validates and Finalizes Registration - Finally, the server is required to perform a series of checks to ensure
that the registration was complete and not tampered with. These include:
1. Verifying that the challenge is the same as the challenge that was sent
2. Ensuring that the origin was the origin expected
3. Validating that the signature over the clientDataHash and the attestation using the certificate chain for that spe-
cific model of the authenticator
7.1.6 Example: Healthcare provider user enrolment
For example, a potential use case from healthcare presented during enrolment are usable. The strate-
could include a healthcare provider’s online enrol- gic goal is to improve the user experience and better
ment processes. The process will first attempt to identify a member at enrolment time in combination
help onboard a new member using customer attri- with other internal authentication processes.
bute information and then determine if the attributes
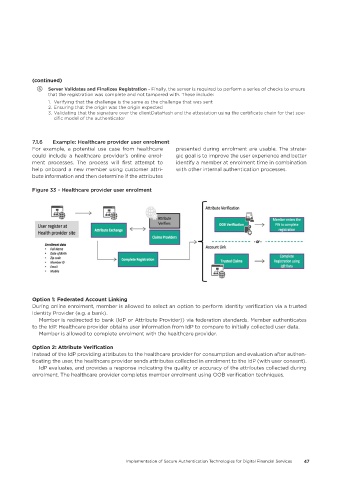
Figure 33 – Healthcare provider user enrolment
Option 1: Federated Account Linking
During online enrolment, member is allowed to select an option to perform identity verification via a trusted
Identity Provider (e.g. a bank).
Member is redirected to bank (IdP or Attribute Provider)) via federation standards. Member authenticates
to the IdP. Healthcare provider obtains user information from IdP to compare to initially collected user data.
Member is allowed to complete enrolment with the healthcare provider.
Option 2: Attribute Verification
Instead of the IdP providing attributes to the healthcare provider for consumption and evaluation after authen-
ticating the user, the healthcare provider sends attributes collected in enrolment to the IdP (with user consent).
IdP evaluates, and provides a response indicating the quality or accuracy of the attributes collected during
enrolment. The healthcare provider completes member enrolment using OOB verification techniques.
Implementation of Secure Authentication Technologies for Digital Financial Services 47