Page 21 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 21
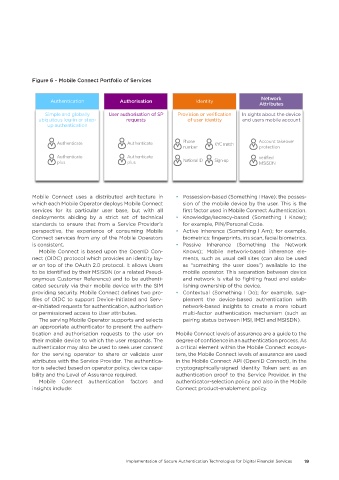
Figure 6 – Mobile Connect Portfolio of Services
Networketwork
N
A
Authenticationuthentication Authorisationuthorisation Identitydentity
I
A
A
Attributesttributes
I
Provision or verification rovision or verification
U
Simple and globally imple and globally User authorisation of SP ser authorisation of SP P In sights about the device n sights about the device
S
u
o
ubiquitous log-in or step-biquitous log-in or step- r requestsequests of user identityf user identity a and users mobile accountnd users mobile account
up authenticationp authentication
u
Phone Account takeover
Authenticate Authenticate KYC match
number protection
Authenticate Authenticate verified
plus plus National ID Sign-up MSISDN
Mobile Connect uses a distributed architecture in • Possession-based (Something I Have); the posses-
which each Mobile Operator deploys Mobile Connect sion of the mobile device by the user. This is the
services for its particular user base, but with all first factor used in Mobile Connect Authentication.
deployments abiding by a strict set of technical • Knowledge/secrecy-based (Something I Know);
standards to ensure that from a Service Provider’s for example, PIN/Personal Code.
perspective, the experience of consuming Mobile • Active Inherence (Something I Am); for example,
Connect services from any of the Mobile Operators biometrics: fingerprints, iris scan, facial biometrics.
is consistent. • Passive Inherence (Something the Network
Mobile Connect is based upon the OpenID Con- Knows); Mobile network-based inherence ele-
nect (OIDC) protocol which provides an identity lay- ments, such as usual cell sites (can also be used
er on top of the OAuth 2.0 protocol. It allows Users as “something the user does”) available to the
to be identified by their MSISDN (or a related Pseud- mobile operator. This separation between device
onymous Customer Reference) and to be authenti- and network is vital to fighting fraud and estab-
cated securely via their mobile device with the SIM lishing ownership of the device.
providing security. Mobile Connect defines two pro- • Contextual (Something I Do); for example, sup-
files of OIDC to support Device-Initiated and Serv- plement the device-based authentication with
er-Initiated requests for authentication, authorisation network-based insights to create a more robust
or permissioned access to User attributes. multi-factor authentication mechanism (such as
The serving Mobile Operator supports and selects pairing status between IMSI, IMEI and MSISDN).
an appropriate authenticator to present the authen-
tication and authorisation requests to the user on Mobile Connect levels of assurance are a guide to the
their mobile device to which the user responds. The degree of confidence in an authentication process. As
authenticator may also be used to seek user consent a critical element within the Mobile Connect ecosys-
for the serving operator to share or validate user tem, the Mobile Connect levels of assurance are used
attributes with the Service Provider. The authentica- in the Mobile Connect API (OpenID Connect), in the
tor is selected based on operator policy, device capa- cryptographically-signed Identity Token sent as an
bility and the Level of Assurance required. authentication proof to the Service Provider, in the
Mobile Connect authentication factors and authenticator-selection policy and also in the Mobile
insights include: Connect product-enablement policy.
Implementation of Secure Authentication Technologies for Digital Financial Services 19