Page 20 - Implementation of Secure Authentication Technologies for Digital Financial Services
P. 20
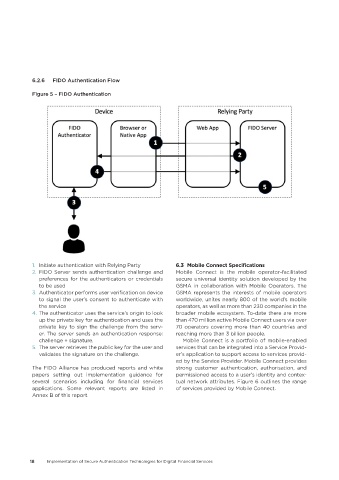
6.2.6 FIDO Authentication Flow
Figure 5 – FIDO Authentication
1. Initiate authentication with Relying Party 6�3 Mobile Connect Specifications
2. FIDO Server sends authentication challenge and Mobile Connect is the mobile operator-facilitated
preferences for the authenticators or credentials secure universal identity solution developed by the
to be used GSMA in collaboration with Mobile Operators. The
3. Authenticator performs user verification on device GSMA represents the interests of mobile operators
to signal the user’s consent to authenticate with worldwide, unites nearly 800 of the world’s mobile
the service operators, as well as more than 230 companies in the
4. The authenticator uses the service’s origin to look broader mobile ecosystem. To-date there are more
up the private key for authentication and uses the than 470 million active Mobile Connect users via over
private key to sign the challenge from the serv- 70 operators covering more than 40 countries and
er. The server sends an authentication response: reaching more than 3 billion people.
challenge + signature. Mobile Connect is a portfolio of mobile-enabled
5. The server retrieves the public key for the user and services that can be integrated into a Service Provid-
validates the signature on the challenge. er’s application to support access to services provid-
ed by the Service Provider. Mobile Connect provides
The FIDO Alliance has produced reports and white strong customer authentication, authorisation, and
papers setting out implementation guidance for permissioned access to a user’s identity and contex-
several scenarios including for financial services tual network attributes. Figure 6 outlines the range
applications. Some relevant reports are listed in of services provided by Mobile Connect.
Annex B of this report.
18 Implementation of Secure Authentication Technologies for Digital Financial Services